VPN > Advanced
915
SonicOS 5.8.1 Administrator Guide
Note Password updates can only be done by LDAP when using Active Directory with TLS
and binding to it using an administrative account, or when using Novell eDirectory.
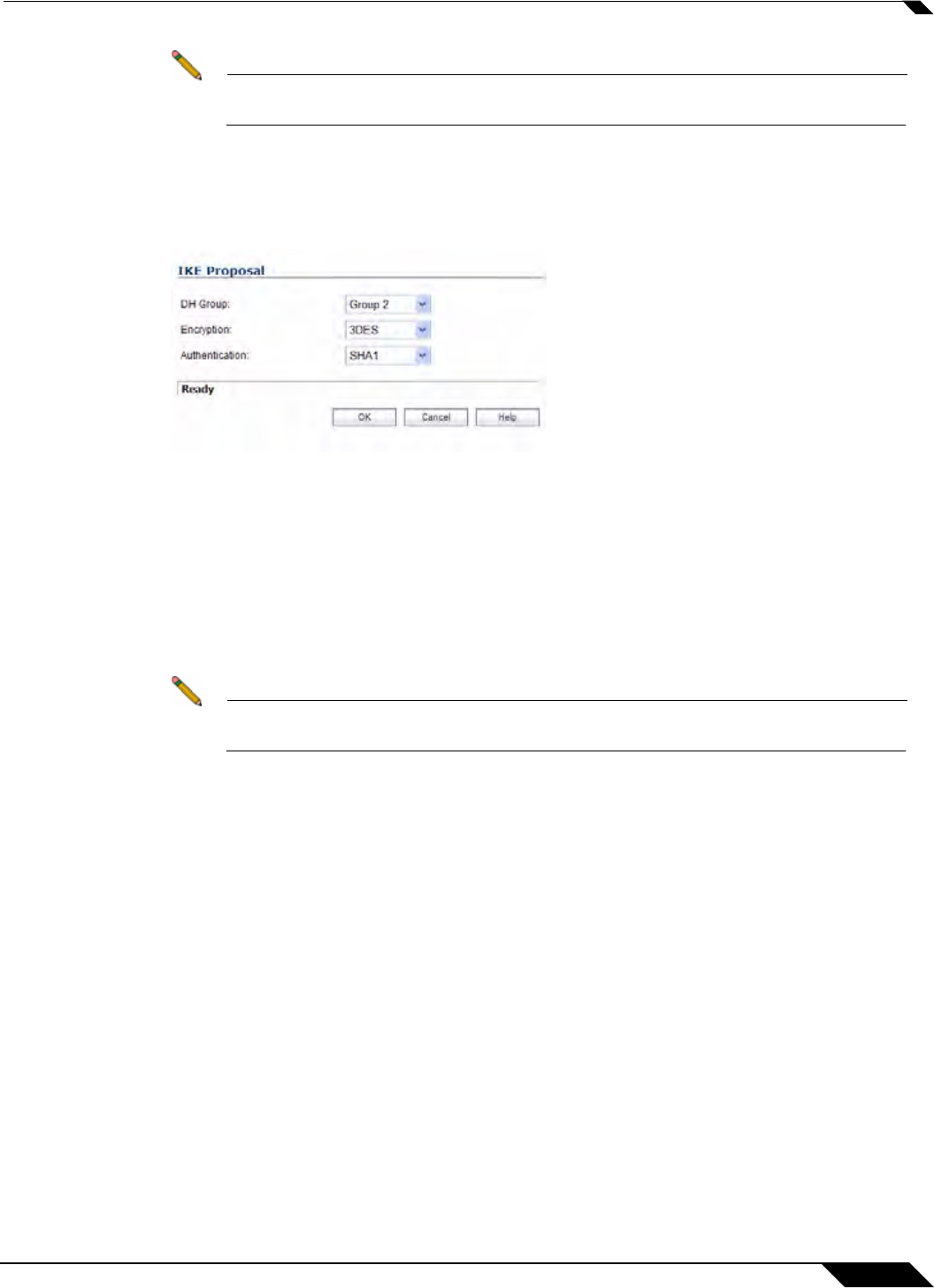
• IKEv2 Dynamic Client Proposal - SonicOS Enhanced firmware versions 4.0 and higher
provide IKEv2 Dynamic Client Support, which provides a way to configure the Internet Key
Exchange (IKE) attributes rather than using the default settings. Clicking the Configure
button launches the Configure IKEv2 Dynamic Client Proposal window.
Previously, only the default settings were supported: Diffie-Hellman (DH) Group 2, the
3DES encryption algorithm, and the SHA1 authentication method. SonicOS now allows the
following IKE Proposal settings:
–
DH Group: 1, 2, 5, or 14
–
Encryption: DES, 3DES, AES-128, AES-192, AES-256
–
Authentication: MD5, SHA1
However, if a VPN Policy with IKEv2 exchange
mode and a 0.0.0.0 IPSec gateway is
defined, you cannot configure these IKE Proposal settings on an individual policy basis.
Note The VPN policy on the remote gateway must also be configured with the same
settings.
Using OCSP with SonicWALL Security Appliances
Online Certificate Status Protocol (OCSP) allows you to check VPN certificate status without
CRLs. This allows timely updates regarding the status of the certificates used on your
SonicWALL.
About OCSP
OCSP is designed to augment or replace Certificate Revocation Lists (CRL) in your Public Key
Infrastructure (PKI) or digital certificate system. The CRL is used to validate the digital
certificates comprised by the PKI. This allows the Certificate Authority (CA) to revoke
certificates before their scheduled expiration date and is useful in protecting the PKI system
against stolen or invalid certificates.
The main disadvantage of Certificate Revocation Lists is the need for frequent updates to keep
the CRL of every client current. These frequent updates greatly increase network traffic when
the complete CRL is downloaded by every client. Depending on the frequency of the CRL
updates, a period of time can exist when a certificate is revoked by the CRL but the client has
not received the CRL update and permits the certificate to be used.


















