Network > Interfaces
196
SonicOS 5.8.1 Administrator Guide
–
If the VLAN ID is allowed, the packet is de-capsulated, the VLAN ID is stored, and the
inner packet (including the IP header) is passed through the full packet handler.
3. Since any number of subnets is supported by L2 Bridging, no source IP spoof checking is
performed on the source IP of the packet. It is possible to configure L2 Bridges to only
support a certain subnet or subnets using Firewall Access Rules.
4. SYN Flood checking is performed.
5. A destination route lookup is performed to the destination zone, so that the appropriate
Firewall Access rule can be applied. Any zone is a valid destination, including the same
zone as the source zone (e.g. LAN to LAN), the Untrusted zone (WAN), the Encrypted
(VPN), Wireless (WLAN), Multicast, or custom zones of any type.
6. A NAT lookup is performed and applied, as needed.
–
In general, the destination for packets entering an L2 Bridge will be the Bridge-Partner
interface (that is, the other side of the bridge). In these cases, no translation will be
performed.
–
In cases where the L2 Bridge Management Address is the gateway, as will sometimes
be the case in Mixed-Mode topologies, then NAT will be applied as need (see the L2
Bridge Path Determination section for more details).
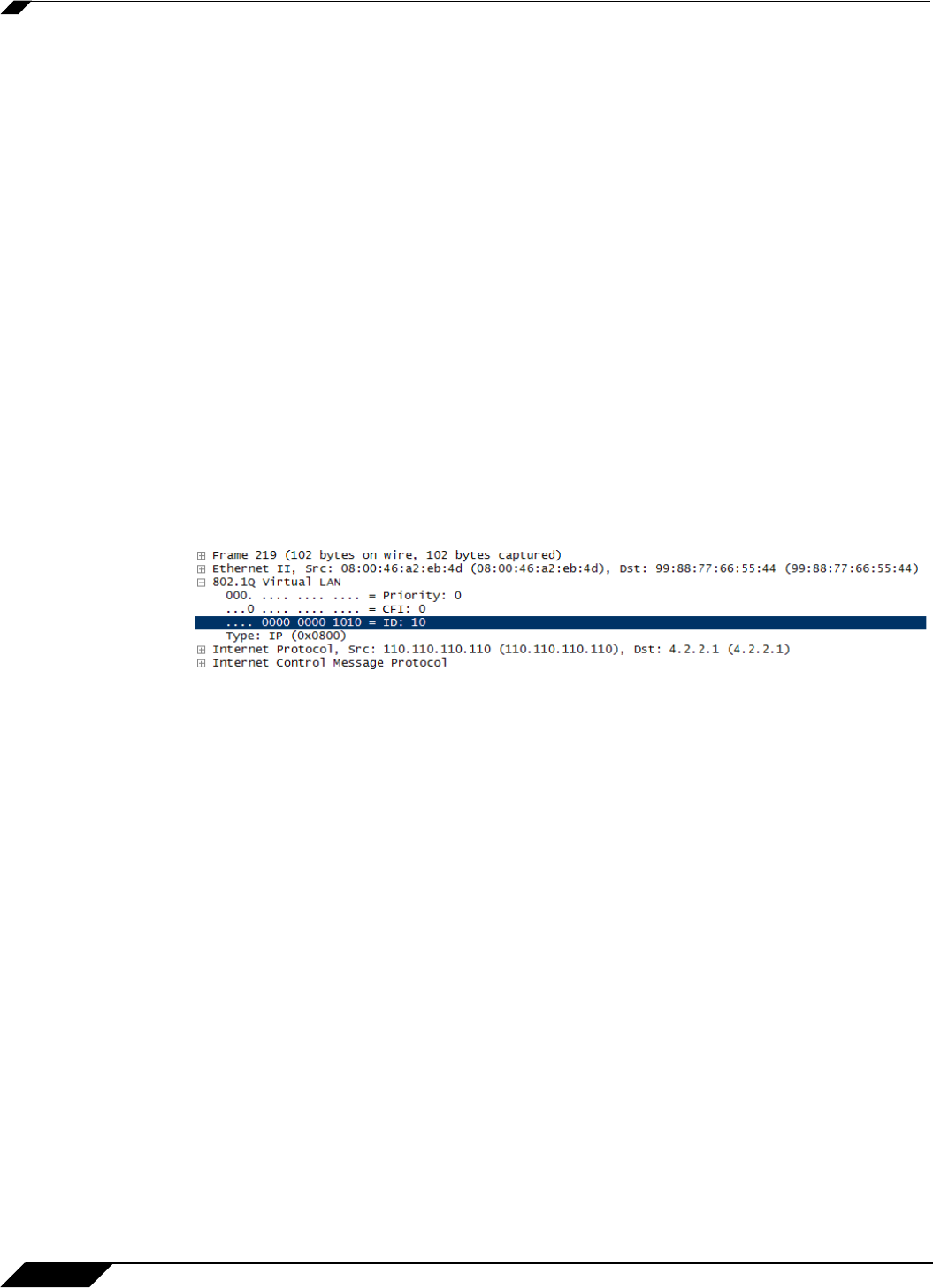
7. Firewall Access Rules are applied to the packet. For example, on SonicWALL NSA series
appliances, the following packet decode shows an ICMP packet bearing VLAN ID 10,
source IP address 110.110.110.110 destined for IP address 4.2.2.1.
It is possible to construct a Firewall Access Rule to control any IP packet, independent of
its VLAN membership, by any of its IP elements, such as source IP, destination IP, or
service type. If the packet is disallowed, it will be dropped and logged. If the packet is
allowed, it will continue.
8. A connection cache entry is made for the packet, and required NAT translations (if any) are
performed.
9. Stateful packet inspection and transformations are performed for TCP, VoIP, FTP, MSN,
Oracle, RTSP and other media streams, PPTP and L2TP. If the packet is disallowed, it will
be dropped and logged. If the packet is allowed, it will continue.
10. Deep packet inspection, including GAV, IPS, Anti-Spyware, CFS and email-filtering is
performed. If the packet is disallowed, it will be dropped and logged. If the packet is
allowed, it will continue. Client notification will be performed as configured.
11. If the packet is destined for the Encrypted zone (VPN), the Untrusted zone (WAN), or some
other connected interface (the last two of which might be the case in Mixed-Mode
Topologies) the packet will be sent via the appropriate path.
12. If the packet is not destined for the VPN/WAN/Connected interface, the stored VLAN tag
will be restored, and the packet (again bearing the original VLAN tag) will be sent out the
Bridge-Partner interface.


















