App Control Use Cases
702
SonicOS 5.8.1 Administrator Guide
Custom Signature
You can create a custom match object that matches any part of a packet if you want to control
traffic that does not have a predefined object type in Application Control. This allows you to
create a custom signature for any network protocol.
For instance, you can create a custom signature to match HTTP GET request packets. You
might use this if you want to prevent Web browsing from your local area network.
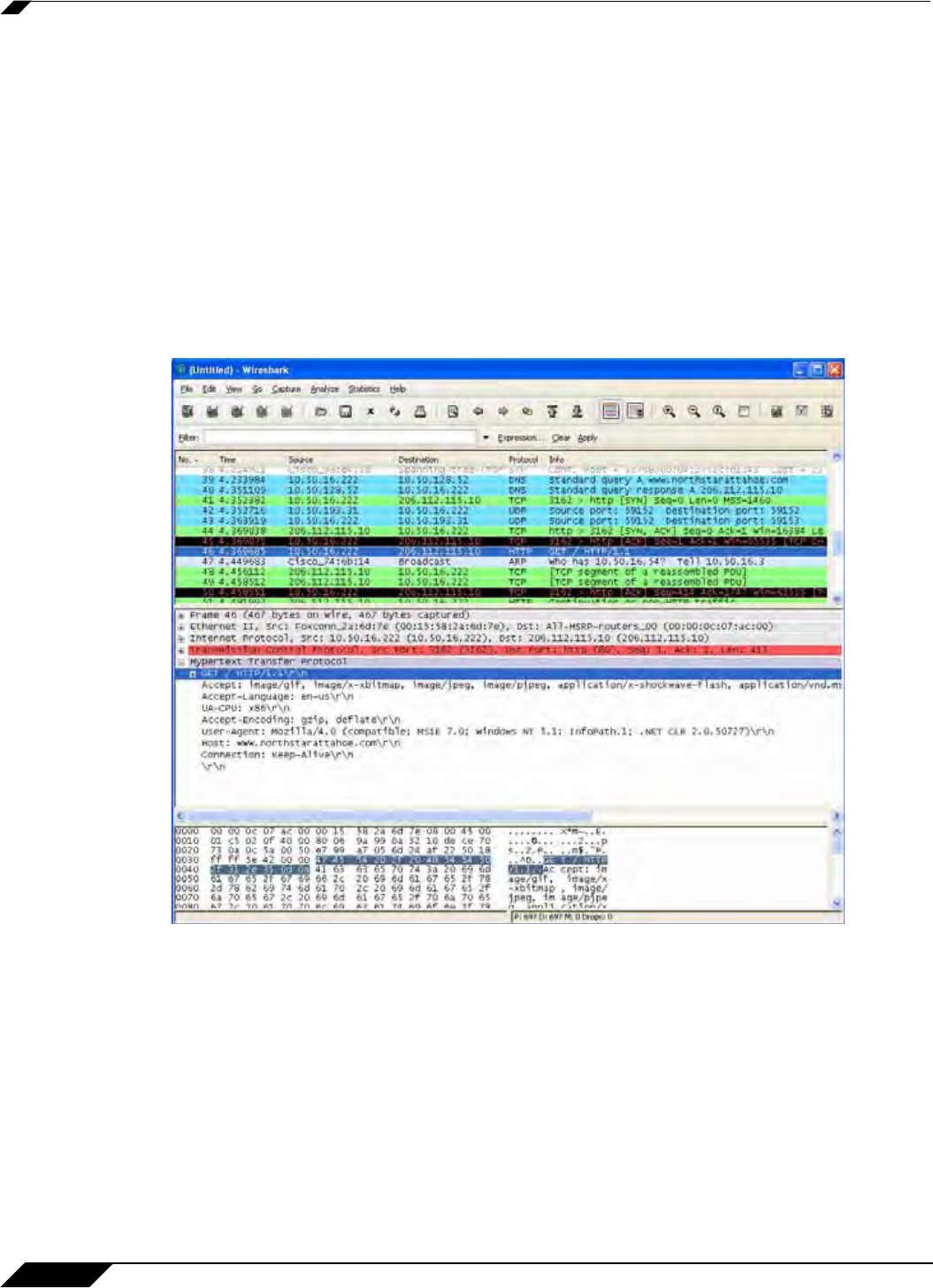
To determine a unique identifier for a HTTP GET packet, you can use the Wireshark network
protocol analyzer to view the packet header. For more information about using Wireshark, see
“Wireshark” on page 674. In Wireshark, capture some packets that include the traffic you are
interested in. In this case, you want to capture a HTTP GET request packet. You can use any
Web browser to generate the HTTP GET request. The following image shows a HTTP GET
request packet displayed by Wireshark.
In the top pane of Wireshark, scroll down to find the HTTP GET packet, and click on that line.
The packet is displayed in the two lower panes. For a SYN packet, the center pane provides a
human-readable interpretation of the packet header, and the actual header bytes are displayed
in hexadecimal in the lower pane.
In the center pane, expand the Hypertext Transfer Protocol section to see the packet payload
and click on the identifier that you want to reference in Application Control. In this case, the
identifier is the GET command in the first three bytes. Click on this to highlight the
corresponding bytes in the lower pane.
You can determine the offset and the depth of the highlighted bytes in the lower pane. Offset
and depth are terms used by Application Control. Offset indicates which byte in the packet to
start matching against, and depth indicates the last byte to match. Using an offset allows very
specific matching and minimizes false positives. When you calculate offset and depth, note that


















