VoIP Call Status
828
SonicOS 5.8.1 Administrator Guide
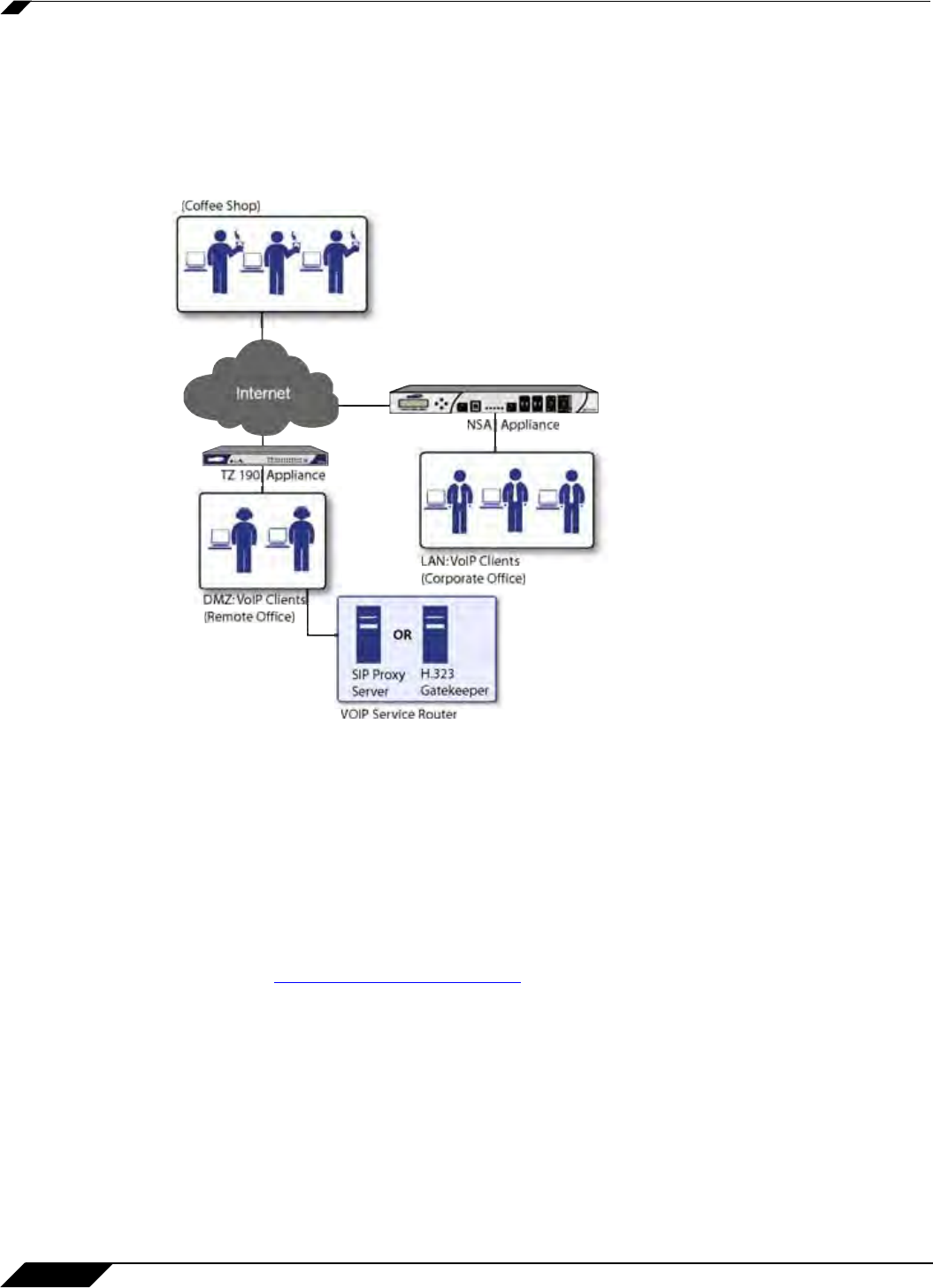
Deployment Scenario 3: Trusted VoIP Service
The organization deploys its own VoIP server on a DMZ or LAN to provide in-house VoIP
services that are accessible to VoIP clients on the Internet or from local network users behind
the security gateway. The following figure shows a trusted VoIP service topology.
For VoIP clients that register with a server on the DMZ or LAN, the SonicWALL security
appliance automatically manages NAT policies and access rules. The SonicWALL security
appliance performs stateful monitoring of registration and permits incoming calls for clients
while they remain registered. No configuration on the VoIP clients is required.
To make a server on the LAN accessible to clients on the WAN:
7. Define a Host address object with the zone and IP address of the server.
8. Define a NAT policy, mapping traffic coming to the SonicWALL security appliance’s public
(WAN) IP address and VoIP service (SIP or H.323 Gatekeeper) to the server.
9. Define access rules allowing VoIP service to pass through the firewall.
10. See the “Using the Public Server Wizard” section for information on configuring this
deployment.
VoIP Call Status
The VoIP > Call Status page provides a listing of currently active VoIP calls. The VoIP Call
Status table displays the following information about the active VoIP connection:
• Caller IP
• Caller-ID
0UBLIC6O)0#LIENTS
.ETWORK3ECURITY!PPLIANCE


















