App Control Use Cases
686
SonicOS 5.8.1 Administrator Guide
You can use this match object in a policy to block browsers that are not MSIE 6.0. For
information about using Wireshark to find a Web browser identifier, see “Wireshark” on
page 674. For information about negative matching, see “Negative Matching” on page 639.
Another example of a use case for controlling Web browser access is a small e-commerce site
that is selling discounted goods that are salvaged from an overseas source. If the terms of their
agreement with the supplier is that they cannot sell to citizens of the source nation, they could
configure Application Control to block access by the in-country versions of the major Web
browsers.
Application Control supports a pre-defined selection of well-known browsers, and you can add
others as custom match objects. Browser blocking is based on the HTTP User Agent reported
by the browser. Your custom match object must contain content specific enough to identify the
browser without creating false positives. You can use Wireshark or another network protocol
analyzer to obtain a unique signature for the desired browser.
HTTP Post Control
You can enhance the security of public facing read-only HTTP servers by disallowing the HTTP
POST method.
First, use Notepad or another text editor to create a new document called Post.htm that
contains the HTML code below. Save the file to your desktop or a convenient location.
<FORM action="http://www.yahoo.com
/" method="post">
<p>Please enter your name: <input type="T
ext" name="FullName"></p>
<input type="submit" value="Submit"> <INPUT
type="reset">
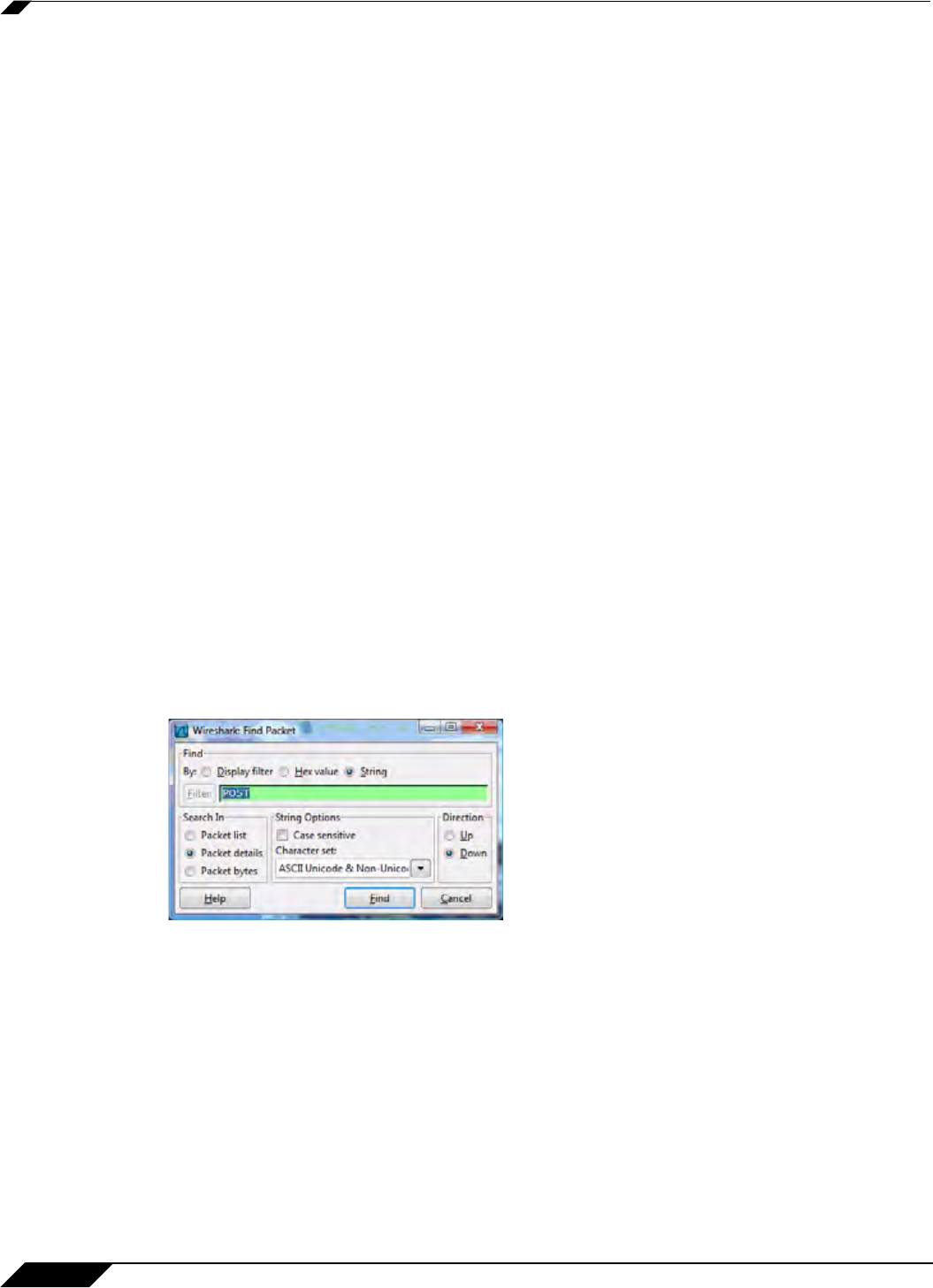
Then open the Wireshark network analyzer and start a capture. For information about using
Wireshark, see Wireshark, page 674. In a browser, open the Post.htm form you just created and
type in your name and then click Submit. Stop the capture.
Using the Wireshark Edit > Find Packet function, search for the string ‘POST’.


















