Security Services > Gateway Anti-Virus
1235
SonicOS 5.8.1 Administrator Guide
Application-level awareness of the type of protocol that is transporting the violation allows
SonicWALL GAV to perform specific actions within the context of the application to gracefully
handle the rejection of the payload.
By default, SonicWALL GAV inspects all inbound HTTP, FTP, IMAP, SMTP and POP3 traffic.
Generic TCP Stream can optionally be enabled to inspect all other TCP based traffic, such as
non-standard ports of operation for SMTP and POP3, and IM and P2P protocols.
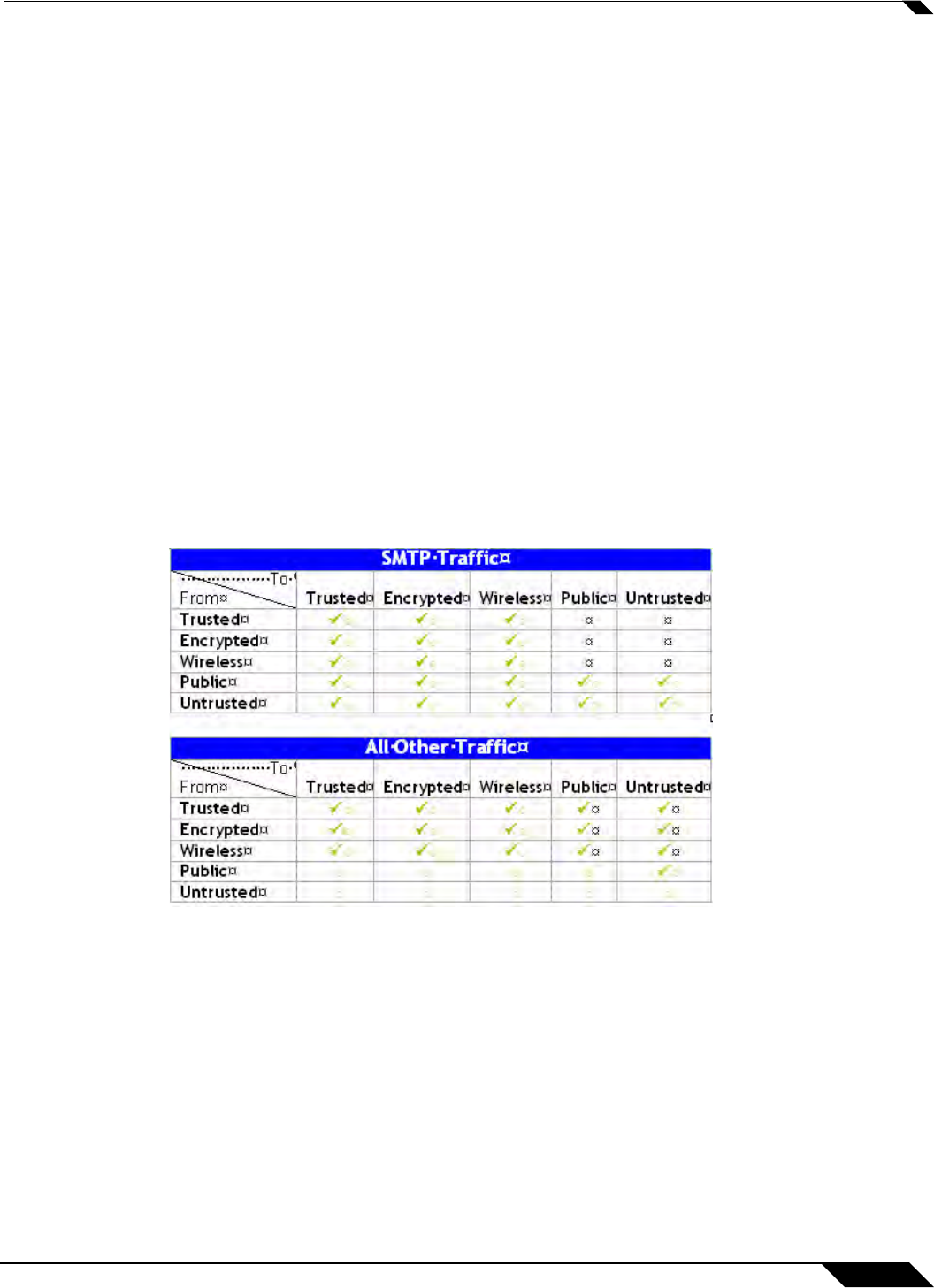
Enabling Inbound Inspection
Within the context of SonicWALL GAV, the Enable Inbound Inspection protocol traffic
handling refers to the following:
• Non-SMTP traffic initiating from a Trusted, Wireless, or Encrypted zone destined to any
zone.
• Non-SMTP traffic from a Public zone destined to an Untrusted zone.
• SMTP traffic initiating from a non-Trusted zone destined to a Trusted, Wireless, Encrypted,
or Public zone.
• SMTP traffic initiating from a Trusted, Wireless, or Encrypted zone destined to a Trusted,
Wireless, or Encrypted zone.
The Enable Inboun
d Inspection protocol traffic handling represented as a table:
Enabling Outbound Inspection
The Enable Outbound Inspection feature is available for HTTP, FTP, SMTP, and TCP traffic.


















