Log > View
1353
SonicOS 5.8.1 Administrator Guide
While data-recorders are good at recording data, they lack the sort of deep-packet inspection
intelligence afforded by IPS/GAV/ASPY/AF. Consider the minimal requirements of effective
data analysis:
• Reliable storage of data
• Effective indexing of data
• Classification of interesting-content
Together, a UTM device (a SonicWALL appliance) and data-recorder (a Solera Networks
appliance)
satisfy the requirements to offer outstanding forensic and data-leakage capabilities.
Distributed Event Detection and Replay
The Solera appliance can search its data-repository, while also allowing the administrator to
define “interesting-content” events on the SonicWALL. The level of logging detail and frequency
of the logging can be configured by the administrator. Nearly all events include Source IP,
Source Port, Destination IP, Destination Port, and Time. SonicOS Enhanced has an extensive
set of log events, including:
• Debug/Informational Events—Connection setup/tear down
• User-events—Administrative access, single sign-on activity, user logins, content filtering
details
• Firewall Rule/Policy Events—Access to and from particular IP:Port combinations, also
identifiable by time
• Interesting-content at the Network or Application Layer—Port-scans, SYN floods, DPI
or AF signature/policy hits
The following is an example of the process of
distributed event detection and replay:
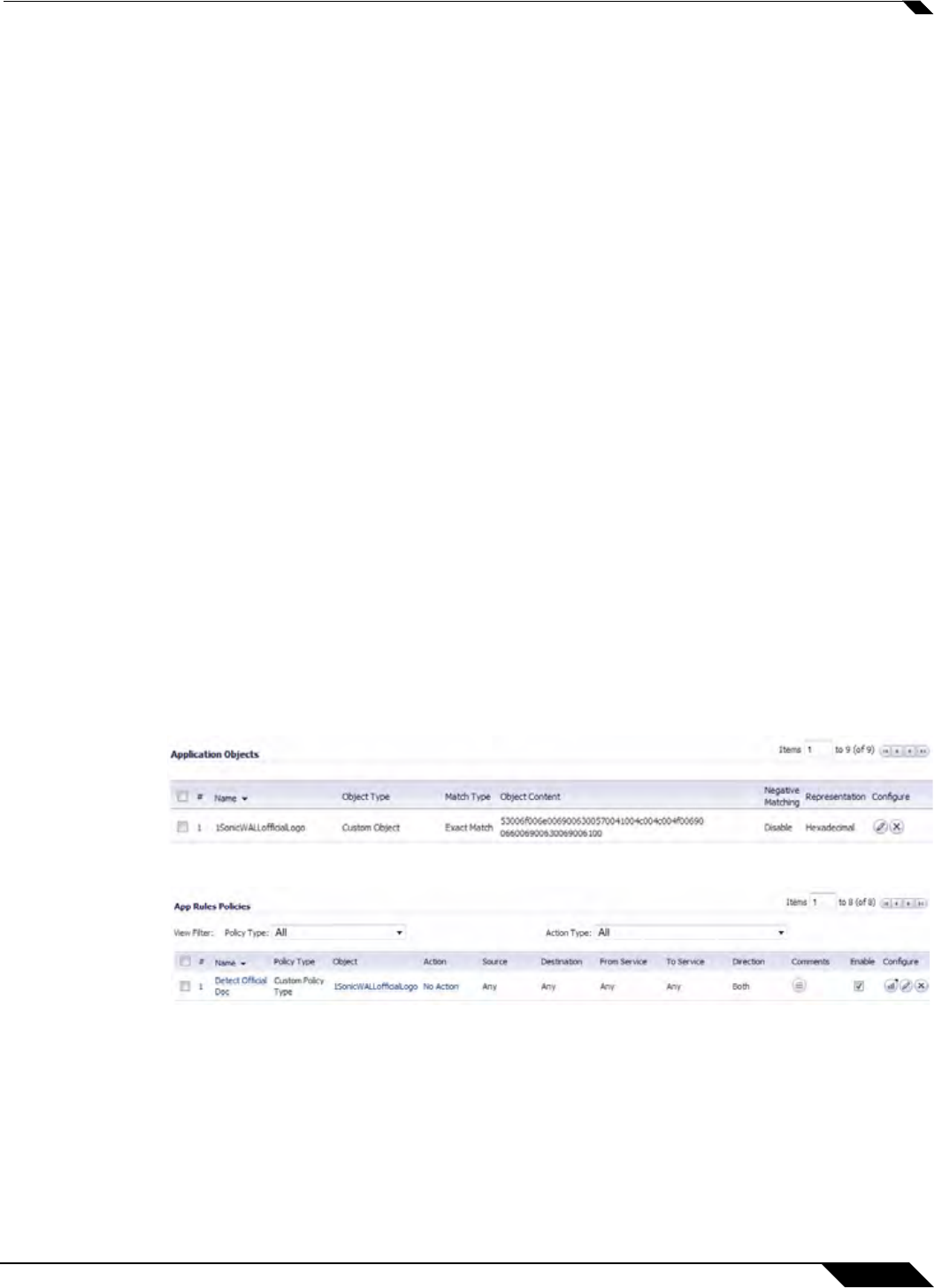
1. The administrator defines the event trigger. For example, an Application Firewall policy is
defined to detect and log the transmission of an official document:
2. A user (at IP address 192.168.19.1) on the network retrieves the file.
3. The event is logged by the SonicWALL.
4. The administrator selects the Recorder icon from the left column of the log entry. Icon/link
only appears in the logs when a NPCS is defined on the SonicWALL (e.g. IP:
[192.168.169.100], Port: [443]). The defined NPCS appliance will be the link’s target. The
link will include the query string parameters defining the desired connection.
5. The NPCS will (optionally) authenticate the user session.


















