App Control Use Cases
704
SonicOS 5.8.1 Administrator Guide
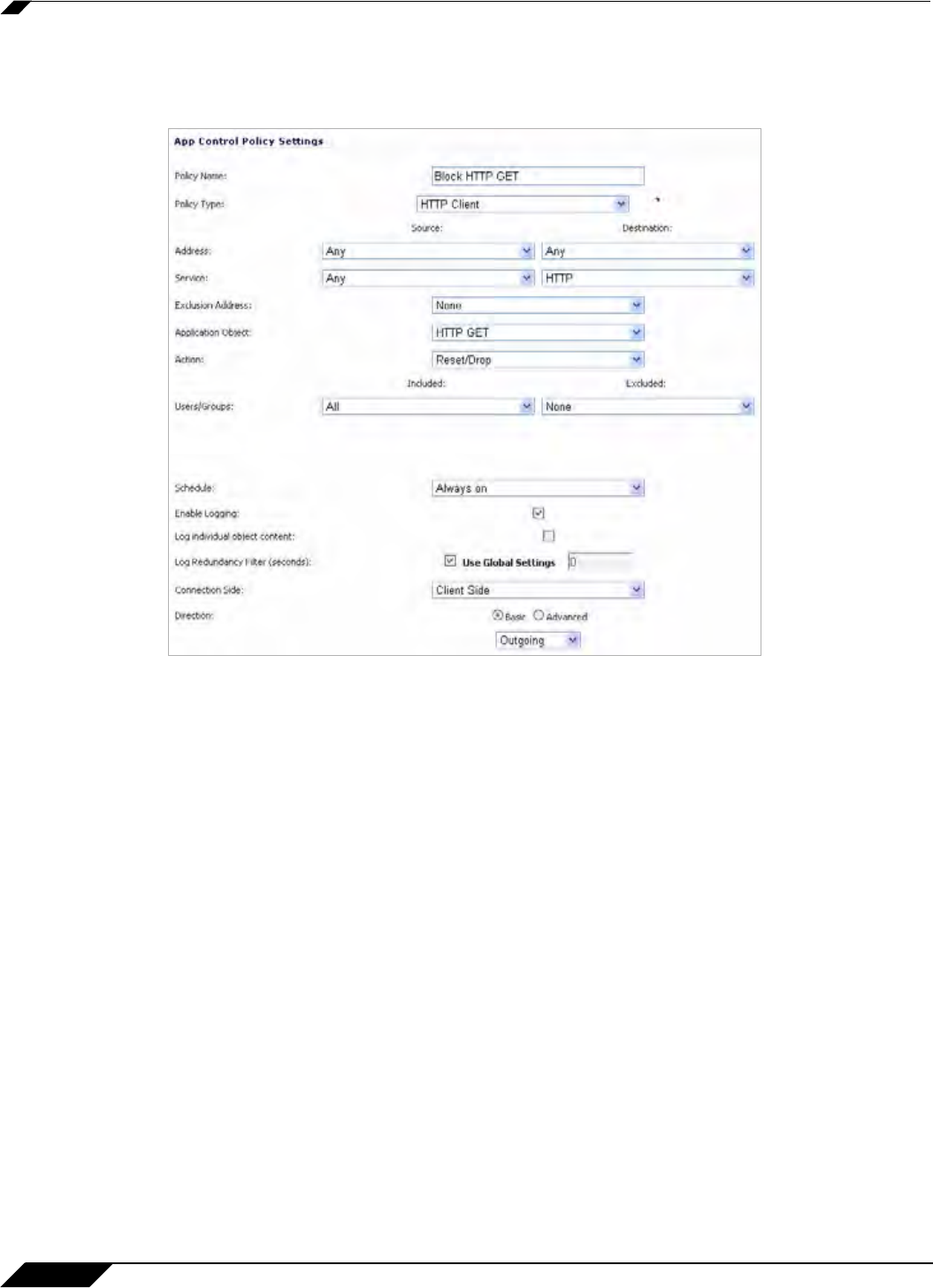
action or a default action such as Reset/Drop. For the Connection Side, select Client Side.
You can also modify other settings. For more information about creating a policy, see
“Configuring an App Rules Policy” on page 660.
Reverse Shell Exploit Prevention
The reverse shell exploit is an attack that you can prevent by using Application Control’s
custom signature capability (See “Custom Signature” on page 702). A reverse shell exploit
could be used by an attacker if he or she is successful in gaining access to your system by
means of a Zero-day exploit. A Zero-day exploit refers to an attack whose signature is not yet
recognized by security software.
In an early stage while still unknown, malicious payloads can pass through the first line of
defense which is the IPS and Gateway Anti-Virus (GAV) running at the Internet gateway, and
even the second line of defense represented by the host-based Anti-Virus software, allowing
arbitrary code execution on the target system.
In many cases, the executed code contains the minimal amount of instructions needed for the
attacker to remotely obtain a command prompt window (with the privileges of the exploited
service or logged on user) and proceed with the penetration from there.
As a common means to circumvent NAT/firewall issues, which might prevent their ability to
actively connect to an exploited system, attackers will make the vulnerable system execute a
reverse shell. In a reverse shell, the connection is initiated by the target host to the attacker
address, using well known TCP/UDP ports for better avoidance of strict outbound policies.
This use case is applicable to environments hosting Windows systems and will intercept
unencrypted connections over all TCP/UDP ports.


















