Log > View
1352
SonicOS 5.8.1 Administrator Guide
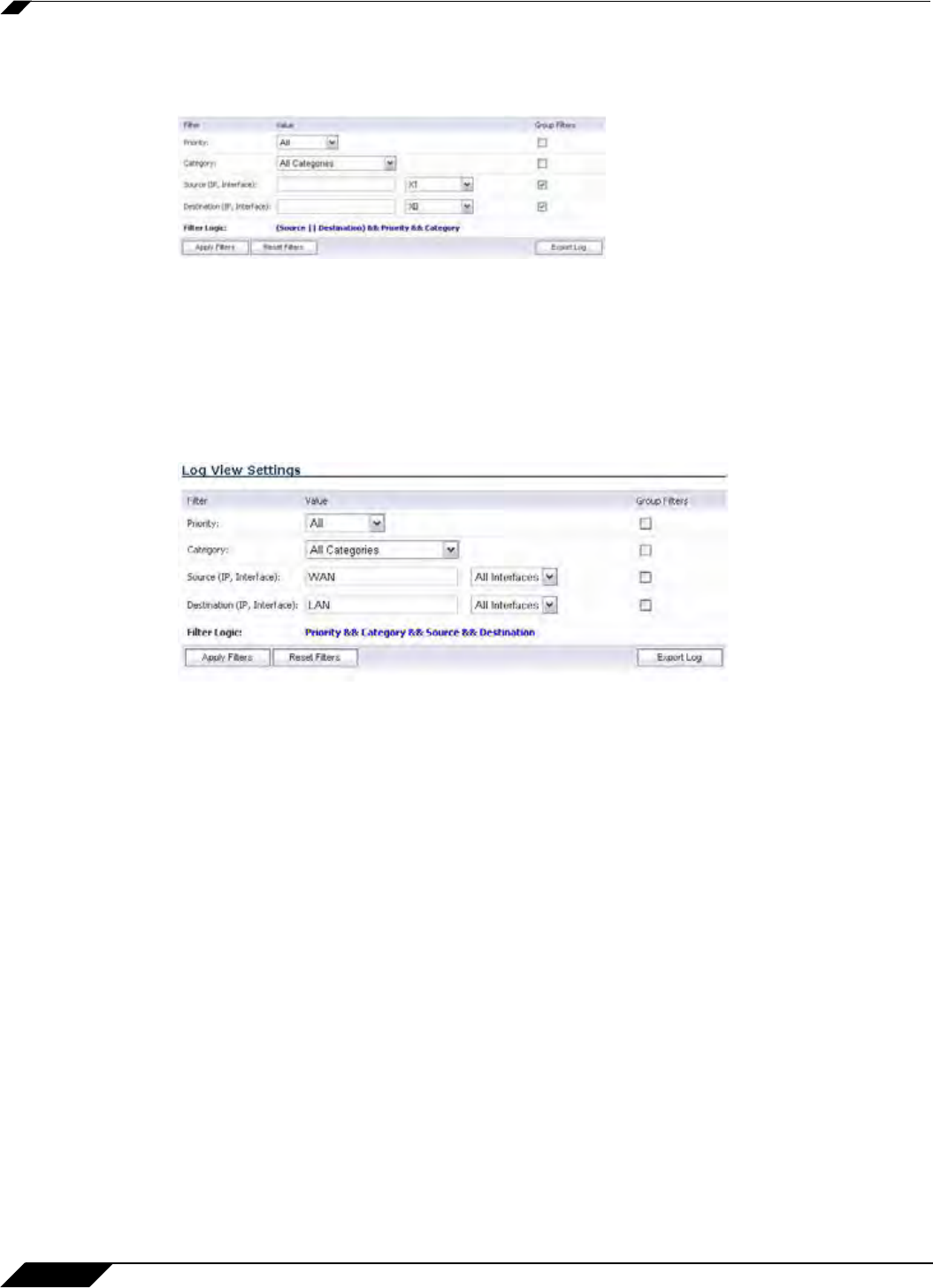
Step 3 Check the Group Filters box next to any two or more criteria to combine them with a logical
OR.
For example, if you enter values for Source IP, D
estination IP, and Protocol, and check
Group Filters next to Source IP and Destination IP, the search string will look for connections
matching:
(So
urce IP OR Destination IP) AND Protocol
Step 4 Click Apply Filter to apply the filter immediately to the Log View Settings table. Click Reset
Filters to clear the filter and display the unfiltered results again.
The following example filters for log events resulting from traffic from the WAN to the LAN:
Log Event Messages
For a complete reference guide of log event messages, refer to the SonicWALL Log Event
Reference Guide.
Deep Packet Forensics
SonicWALL UTM appliances have configurable deep-packet classification capabilities that
intersect with forensic and content-management products. While the SonicWALL can reliably
detect and prevent any ‘interesting-content’ events, it can only provide a record of the
occurrence, but not the actual data of the event.
Of equal importance are diagnostic applications where the interesting-content is traffic that is
being unpredictably handled or inexplicably dropped.
Although the SonicWALL can achieve interesting-content using our Enhanced packet capture
diagnostic tool, data-recorders are application-specific appliances designed to record all the
packets on a network. They are highly optimized for this task, and can record network traffic
without dropping a single packet.


















