Network > Address Objects
312
SonicOS 5.8.1 Administrator Guide
Using an Internal DNS Server for FQDN-based Access Rules
It is common for dynamically configured (DHCP) network environments to work in combination
with internal DNS servers for the purposes of dynamically registering internal hosts – a common
example of this is Microsoft’s DHCP and DNS services. Hosts on such networks can easily be
configured to dynamically update DNS records on an appropriately configured DNS server (for
example, see the Microsoft Knowledgebase article “How to configure DNS dynamic updates in
Windows Server 2003” at http://support.microsoft.com/kb/816592/en-us).
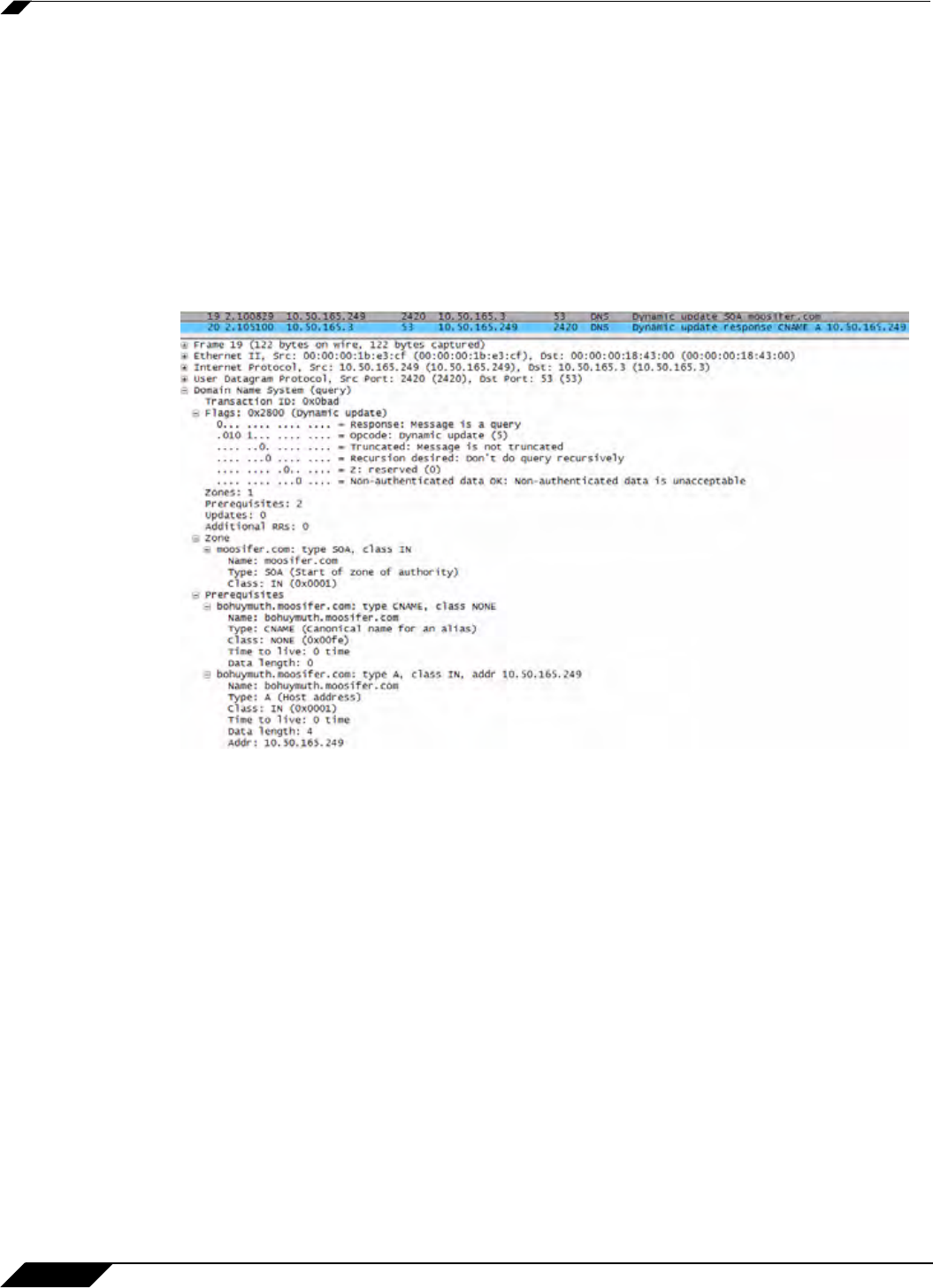
The following illustrates a packet dissection of a typical DNS dynamic update process, showing
the dynamically configured host 10.50.165.249 registering its full hostname
bohuymuth.moosifer.com with the (DHCP provided) DNS server 10.50.165.3:
In such environments, it could prove useful to employ FQDN AOs to control access by
hostname. This would be most applicable in networks where hostnames are known, such as
where hostname lists are maintained, or where a predictable naming convention is used.
Controlling a Dynamic Host’s Network Access by MAC Address
Since DHCP is far more common than static addressing in most networks, it is sometimes
difficult to predict the IP address of dynamically configured hosts, particularly in the absence of
dynamic DNS updates or reliable hostnames. In these situations, it is possible to use MAC
Address Objects to control a host’s access by its relatively immutable MAC (hardware) address.
Like most other methods of access control, this can be employed either inclusively, for
example, to deny access to/for a specific host or group of hosts, or exclusively, where only a
specific host or group of hosts are granted access, and all other are denied. In this example,
we will illustrate the latter.
Assuming you had a set of DHCP-enabled wireless clients running a proprietary operating
system which precluded any type of user-level authentication, and that you wanted to only allow
these clients to access an application-specific server (e.g. 10.50.165.2) on your LAN. The
WLAN segment is using WPA-PSK for security, and this set of clients should only have access


















