User Management
1049
SonicOS 5.8.1 Administrator Guide
• The domain components all use “dc=”
If the “User tree for login to server” field is given as a dn, you can also select this option
if the bind dn conforms to the first bullet above, but not to the second and/or the third
bullet.
–
Give bind distinguished name – Select this option if the bind dn does not conform to
the first bullet above (if the first name component does not begin with “cn=”). This option
can always be selected if the dn is known. You must provide the bind dn explicitly if the
bind dn does not conform to the first bullet above.
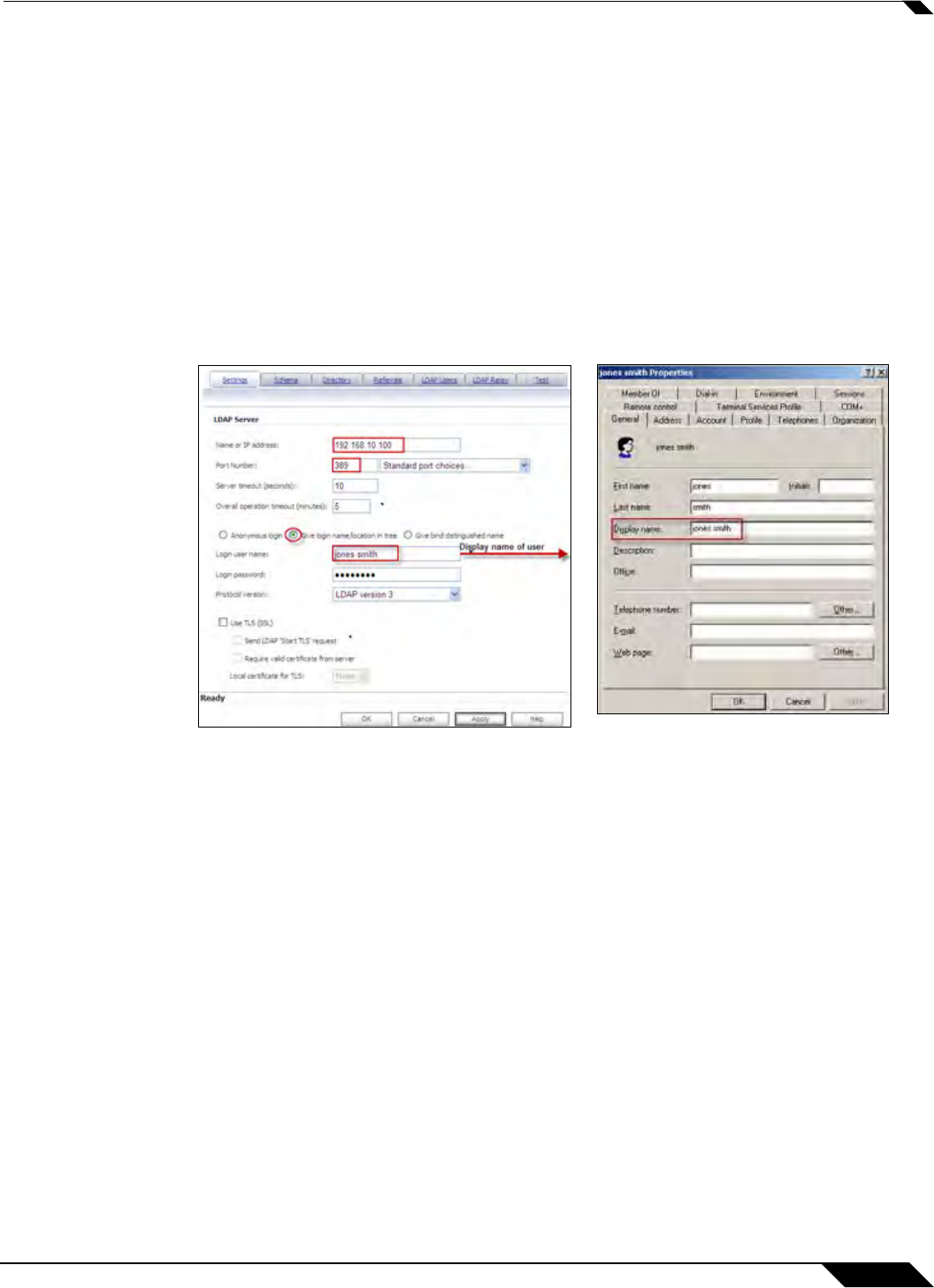
• Login user name – Specify a user name that has rights to log in to the LDAP directory. The
login name will automatically be presented to the LDAP server in full ‘dn’ notation. This can
be any account with LDAP read privileges (essentially any user account) – Administrative
privileges are not required. Note that this is the user’s name, not their login ID (e.g. Jones
Smith rather than jsmith).
• Login password – The password for the user account specified above.
• Protocol version – Select either LDAPv3 or LDAPv2. Most modern implementations of
LDAP, including Active Directory, employ LDAPv3.
• Use TLS – Use Transport Layer Security (SSL) to log in to the LDAP server. It is strongly
recommended that TLS be used to protected the username and password information that
will be sent across the network. Most modern implementations of LDAP server, including
Active Directory, support TLS. Deselecting this default setting will display an alert that you
must accept to proceed.
• Send LDAP ‘Start TLS’ Request – Some LDAP server implementations support the Start
TLS directive rather than using native LDAP over TLS. This allows the LDAP server to listen
on one port (normally 389) for LDAP connections, and to switch to TLS as directed by the
client. Active Directory does not use this option, and it should only be selected if required
by your LDAP server.
• Require valid certificate from server – Validates the certificate presented by the server
during the TLS exchange, matching the name specified above to the name on the
certificate. Deselecting this default option will present an alert, but exchanges between the
SonicWALL and the LDAP server will still use TLS – only without issuance validation.


















