Firewall Settings > QoS Mapping
762
SonicOS 5.8.1 Administrator Guide
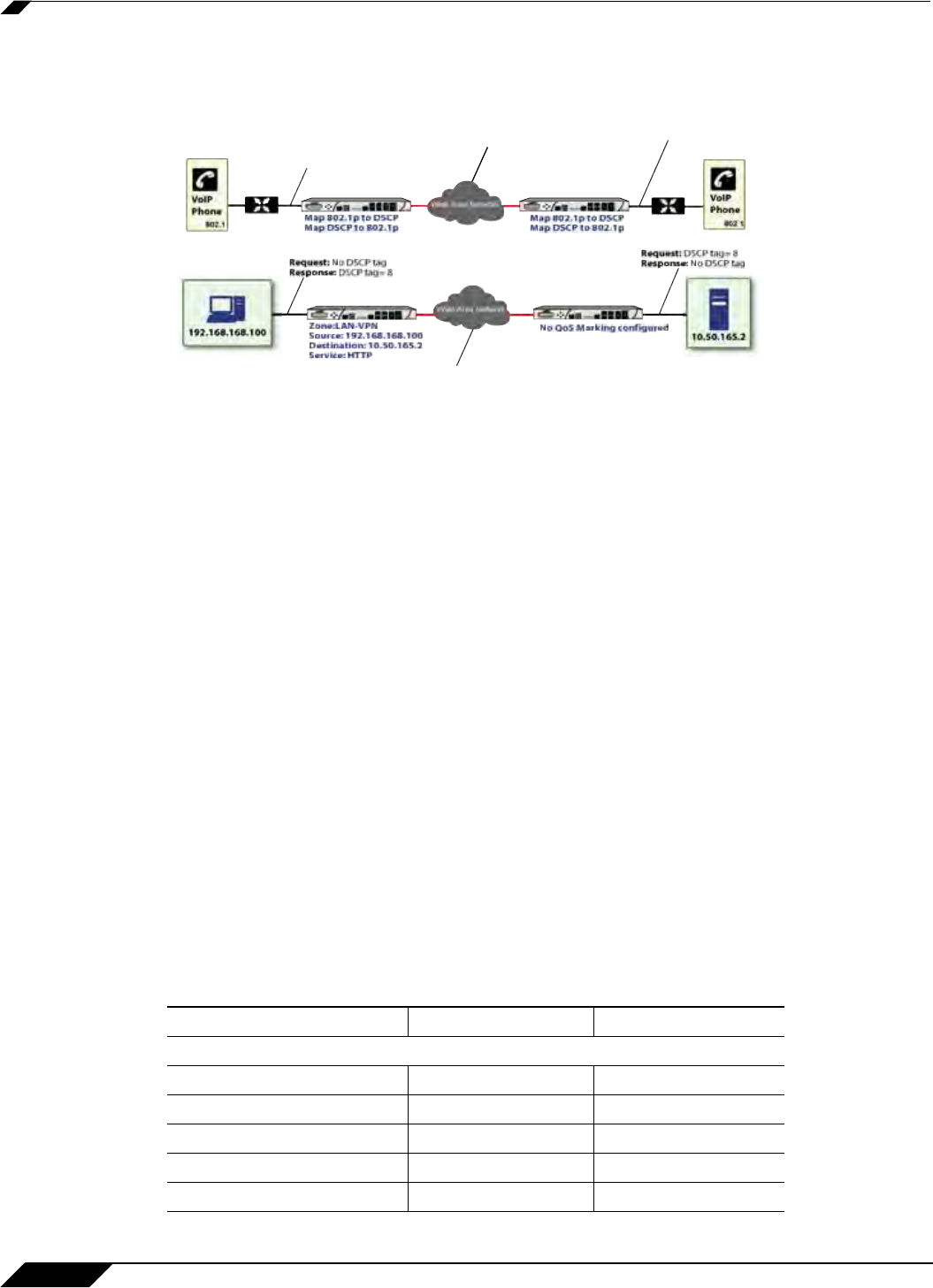
For example, refer to the following figure which provides a bi-directional DSCP tag action.
HTTP access from a Web-browser on 192.168.168.100 to the Web server on 10.50.165.2 will
result in the tagging of the inner (payload) packet and the outer (encapsulating ESP) packets
with a DSCP value of 8. When the packets emerge from the other end of the tunnel, and are
delivered to 10.50.165.2, they will bear a DSCP tag of 8. When 10.50.165.2 sends response
packets back across the tunnel to 192.168.168.100 (beginning with the very first SYN/ACK
packet) the Access Rule will tag the response packets delivered to 192.168.168.100 with a
DSCP value of 8.
This behavior applies to all four QoS action settings for both DSCP and 802.1p marking.
One practical application for this behavior would be configuring an 802.1p marking rule for
traffic destined for the VPN zone. Although 802.1p tags cannot be sent across the VPN, reply
packets coming back across the VPN can be 802.1p tagged on egress from the tunnel. This
requires that 802.1p tagging is active of the physical egress interface, and that the [Zone] >
VPN Access Rule has an 802.1p marking action other than None.
After ensuring 802.1p compatibility with your relevant network devices, and enabling 802.1p
marking on applicable SonicWALL interfaces, you can begin configuring Access Rules to
manage 802.1p tags.
Referring to the following figure, the Remote Site 1 network could have two Access Rules
configured as follows:
6O)0
6O)0
$3#0TAG
./$3#0TAG
PTAG
$3#0TAG
PTAG
.ETWORK3ECURITY!PPLIANCE
Setting Access Rule 1 Access Rule 2
General Tab
Action Allow Allow
From Zone LAN VPN
To Zone VPN LAN
Service VOIP VOIP
Source Lan Primary Subnet Main Site Subnets


















