User Management
1080
SonicOS 5.8.1 Administrator Guide
network may be blocking them. For example, if you have an Access Control List set on a router
in your network to allow NetAPI from the agent’s IP address only, that ACL will block the probes
to the NetAPI port from the appliance.
Probe test mode is useful for initial SSO deployment
and troubleshooting. When Probe test
mode is enabled, you can analyze the behavior by:
–
Checking the agent statistics for probe failures
–
Monitoring the console port for warnings that probes failed when SSO worked; these
messages indicate the host address
If the statistics show 100% probe failures, then something is wrong in the network. If they show
inter
mittent failures, you can try varying the Probe timeout setting to see if it helps.
Step 19 To use LDAP to retrieve user information, select the Use LDAP to retrieve user group
information radio button. Click Configure to configure the LDAP settings. The LDAP
Configuration page displays. For configuration information for this page, refer to “Advanced
LDAP Configuration” on page 1090.
Step 20 To use locally configured user group settings, select the Local configuration radio button.
Step 21 In the Polling rate (minutes) field, enter a polling interval, in minutes. The security appliance
will poll the workstation running SSO Agent once every interval to verify that users are still
logged on. The default is 1.
Step 22 In the Hold time after (minutes) field, enter a time, in minutes, that the security appliance will
wait before trying again to identify traffic after an initial failure to do so. This feature rate-limits
requests to the agent. The default is 1.
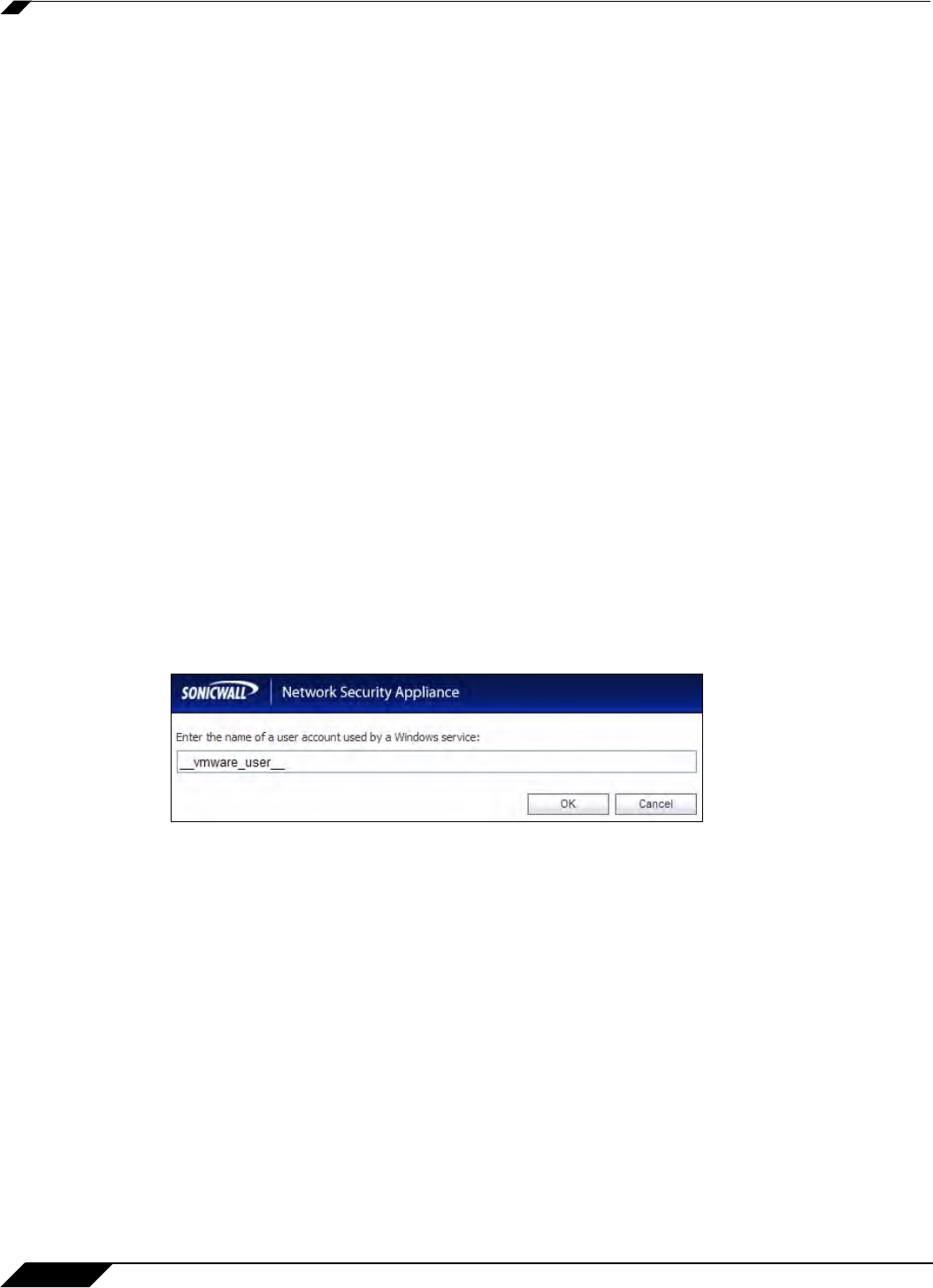
Step 23 To populate the User names used by Windows services list, click the Add button. In the
Service User name dialog box, type the service login name (the simple name only, without the
domain or PC name) into the Enter the name of a user account used by a Windows service
field and then click OK.
The purpose of this list is to distinguish the login names used by Windows services from real
user logins. When the SSO agent queries Windows to find the user logged into a computer,
Windows actually returns a list of user accounts that are/have been logged in to the computer
and does not distinguish user logins from service logins, hence giving the SSO agent no way
to determine that a login name belongs to a service. This may result in the SSO agent
incorrectly reporting a service name instead of the actual user name.
You can enter up to 64 login names here that may be used by services on end-user computers.
The SSO agent will ignore any logins using these names.
If, when using Single Sign On, you see unexpected user names shown on the Users > Status
page, or logs of user login or user login failure with unexpected user names, those may be due
to Windows service logins and those user names should be configured here so that the SSO
agent will know to ignore them.
In cases where there are multiple SonicWALL appliances communicating with an SSO agent,
the list of service account names should be configured on only one of them. The effect of
configuring multiple lists on different appliances is undefined.
