Firewall Settings > SSL Control
783
SonicOS 5.8.1 Administrator Guide
mismatch elicits a browser alert, it is not always a sure sign of deception. For example, if a
client browses to https://mysonicwall.com, which resolves to the same IP address as
www.mysonicwall.com, the server will present its certificate bearing the subject CN of
www.mysonicwall.com. An alert will be presented to the client, despite the total legitimacy
of the connection.
• Certificate Authority (CA) - A Certificate Authority (CA) is a trusted entity that has the
ability to sign certificates intended, primarily, to validate the identity of the certificate’s
subject. Well-known certificate authorities include VeriSign, Thawte, Equifax, and Digital
Signature Trust. In general, for a CA to be trusted within the SSL framework, its certificate
must be stored within a trusted store, such as that employed by most Web-browsers,
operating systems and run-time environments. The SonicOS trusted store is accessible
from the System > Certificates page. The CA model is built on associative trust, where the
client trusts a CA (by having the CA's certificate in its trusted store), the CA trusts a subject
(by having issued the subject a certificate), and therefore the client can trust the subject.
• Untrusted CA – An untrusted CA is a CA that is not contained in the trusted store of the
client. In the case of SSL Control, an untrusted CA is any CA whose certificate is not
present in System > Certificates.
• Self-Signed Certificates – Any certificate where the issuer’s common-name and the
subject’s common-name are the same, indicating that the certificate was self-signed.
• Virtual Hosting – A method employed by Web servers to host more than one website on
a single server. A common implementation of virtual hosting is name-based (Host-header)
virtual hosting, which allows for a single IP address to host multiple websites. With Host-
header virtual hosting, the server determines the requested site by evaluating the “Host:”
header sent by the client. For example, both www.website1.com and www.website2.com
might resolve to 64.41.140.173. If the client sends a “GET /” along with “Host:
www.website1.com”, the server can return content corresponding to that site.
Host-header virtual hosting is generally not employed
in HTTPS because the host header
cannot be read until the SSL connection is established, but the SSL connection cannot be
established until the server sends its Certificate. Since the server cannot determine which
site the client will request (all that is known during the SSL handshake is the IP address) it
cannot determine the appropriate certificate to send. While sending any certificate might
allow the SSL handshake to commence, a certificate name (subject) mismatch will trigger
a browser alert.
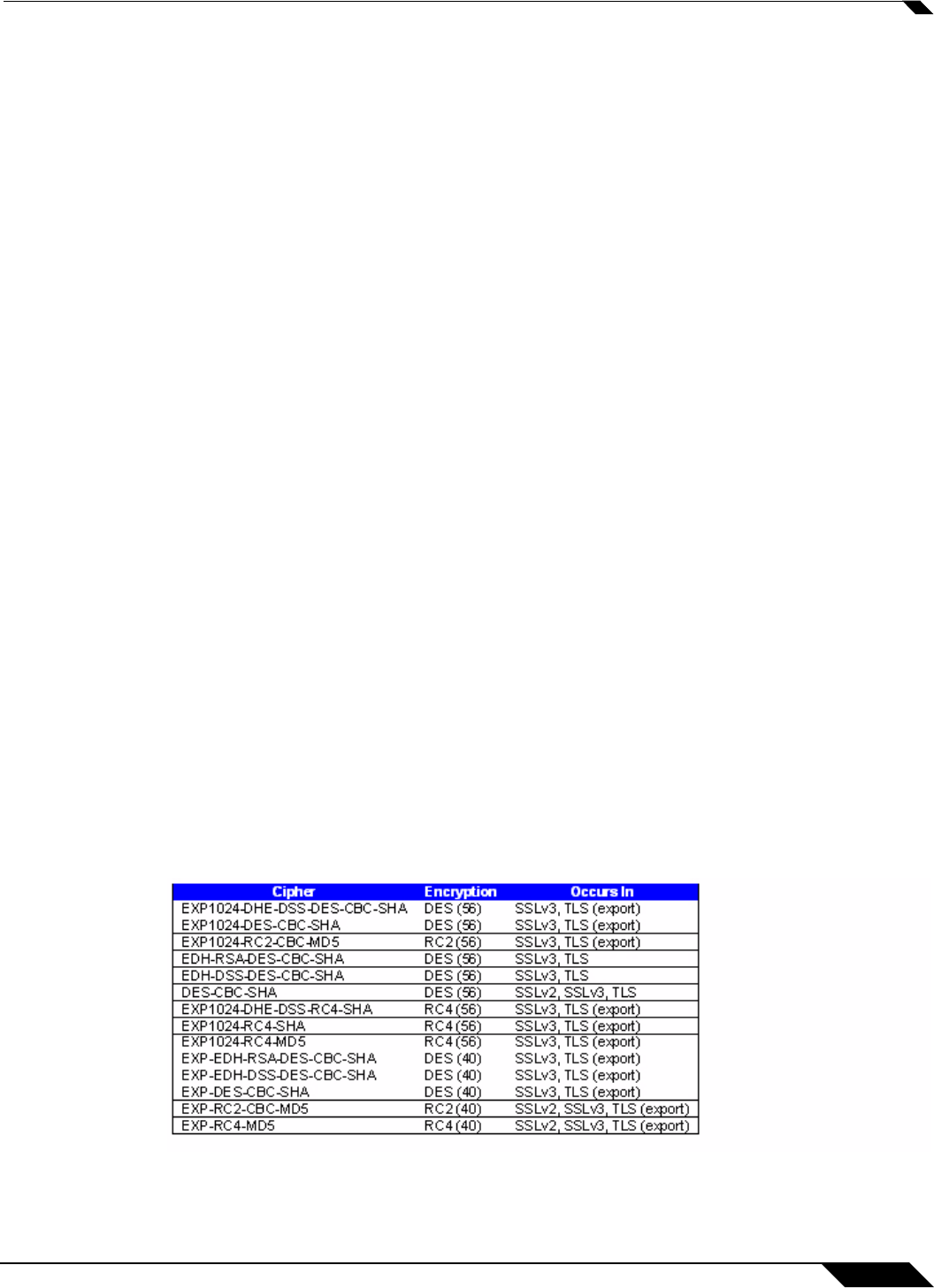
• Weak Ciphers – Relatively weak symmetric cryptography ciphers. Ciphers are classified
as weak when they are less than 64 bits. For the most part, export ciphers are weak ciphers.
The following is a list of common weak ciphers:


















