User Management
1050
SonicOS 5.8.1 Administrator Guide
• Local certificate for TLS – Optional, to be used only if the LDAP server requires a client
certificate for connections. Useful for LDAP server implementations that return passwords
to ensure the identity of the LDAP client (Active Directory does not return passwords). This
setting is not required for Active Directory.
If your network uses multiple LDAP/AD server
s with referrals, then select one as the
primary server (probably the one that holds the bulk of the users) and use the above
settings for that server. It will then refer the SonicWALL on to the other servers for users in
domains other than its own. For the SonicWALL to be able to log in to those other servers,
each server must have a user configured with the same credentials (user name, password
and location in the directory) as the login to the primary server. This may entail creating a
special user in the directory for the SonicWALL login. Note that only read access to the
directory is required.
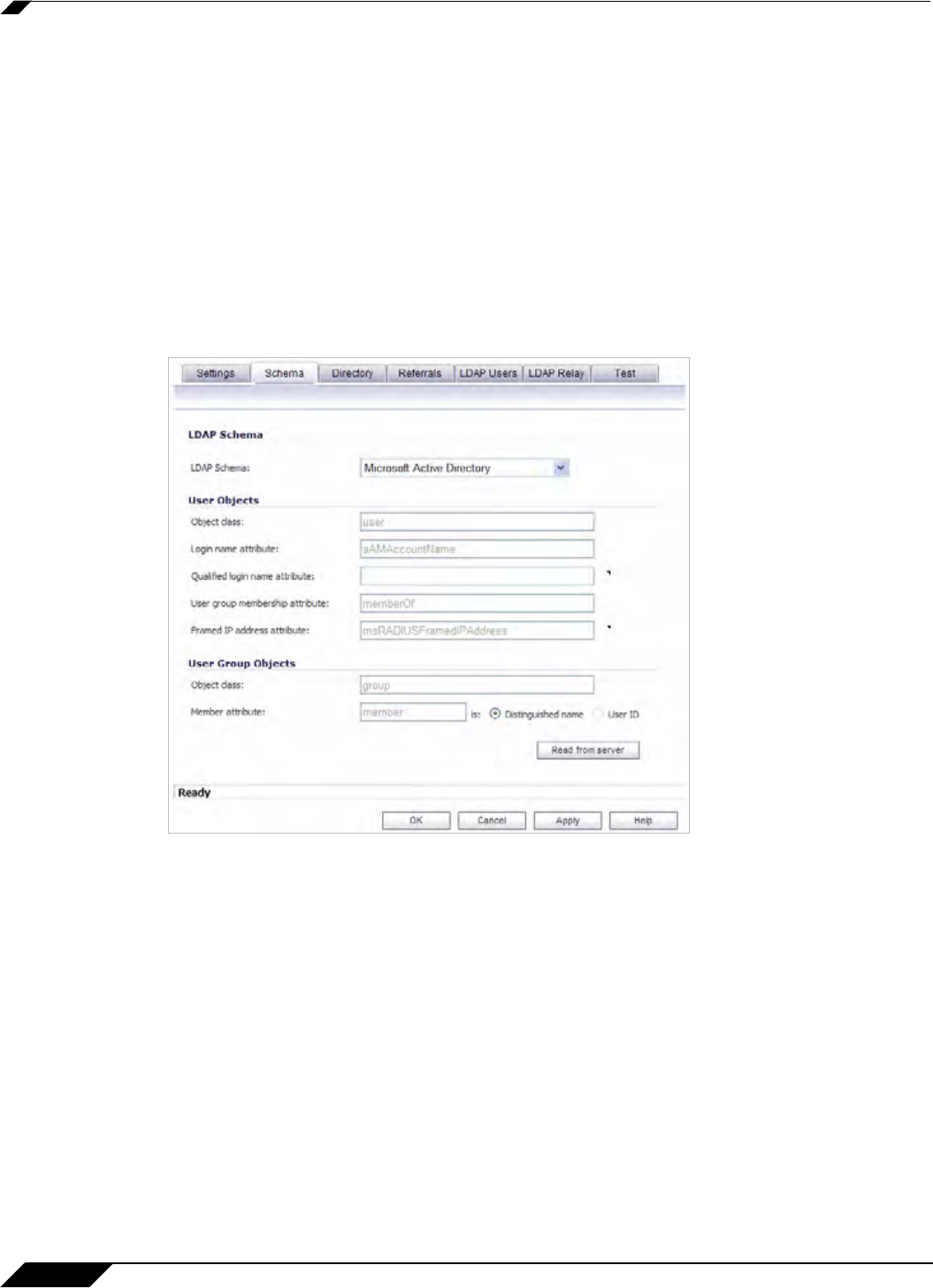
Step 6 On the Schema tab, configure the following fields:
• LDAP Schema – Select one of the following:
–
Microsoft Active Directory
–
RFC2798 inetOrgPerson
–
RFC2307 Network Information Service
–
Samba SMB
–
Novell eDirectory
–
User defined
Selecting any of the predefined schemas will
automatically populate the fields used by
that schema with their correct values. Selecting User defined will allow you to specify
your own values – use this only if you have a specific or proprietary LDAP schema
configuration.
• Object class – Select the attribute that represents the individual user account to which the
next two fields apply.


















