User Management
1109
SonicOS 5.8.1 Administrator Guide
That can be done in one of two ways. The source zone is shown as LAN here, but can be any
applicable zone(s):
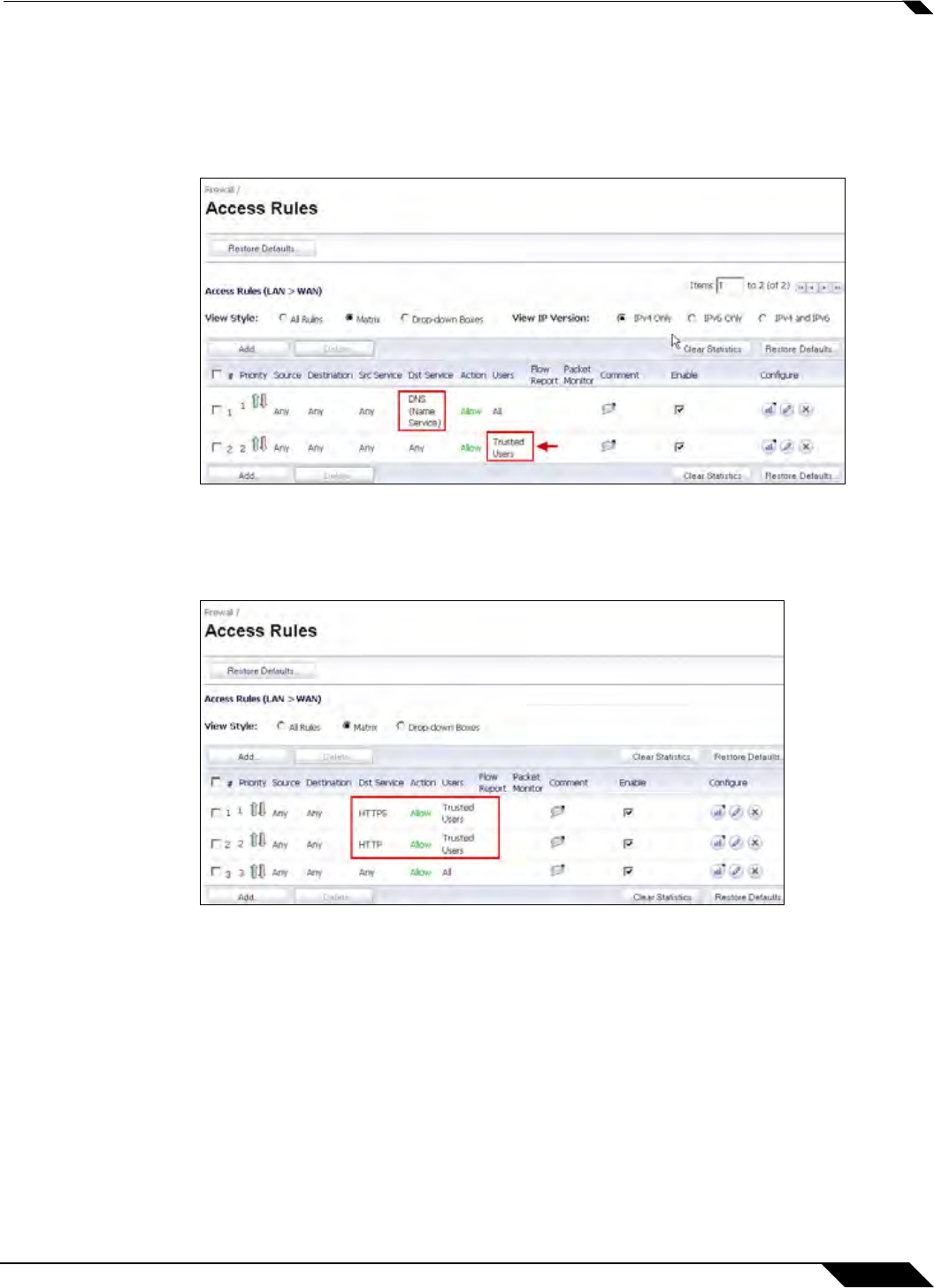
1. Change Users Allowed in the default LAN -> WAN rule to Everyone or Trusted Users.
These are authenticated users. Then add rules to allow out traffic that you do not want to
be blocked for unidentified users (such as DNS, email, ...) with Users Allowed set to All.
2. Leave the default LAN -> WAN rule allowing All users, and add a rule to allow HTTP and
HTTPS from addresses Any to Any with Users Allowed set to Everyone or Trusted Users.
You can also include other services along with HTTP/HTTPS if you do not want those being
used by unauthenticated users.
Of these, option 1 is the more secure option, but
is also the more likely to cause problems by
blocking unforeseen things that should be allowed access without authentication.
Allowing ICMP and DNS Pings from a Terminal Server
In Windows, outgoing ICMP pings from users on the Terminal Server are not sent via a socket
and so are not seen by the TSA, and hence the appliance will receive no notifications for them.
Therefore, if firewall rules are using user level authentication and pings are to be allowed
through, you must create separate access rules to allow them from “All”.
Similarly, outgoing user requests using Fully Qualified Domain Names (FQDN) rather than IP
addresses require that DNS traffic be allowed through. To allow Terminal Server users to use
FQDNs, you must create a firewall access rule that allows DNS traffic from “All”.


















