Network > Interfaces
260
SonicOS 5.8.1 Administrator Guide
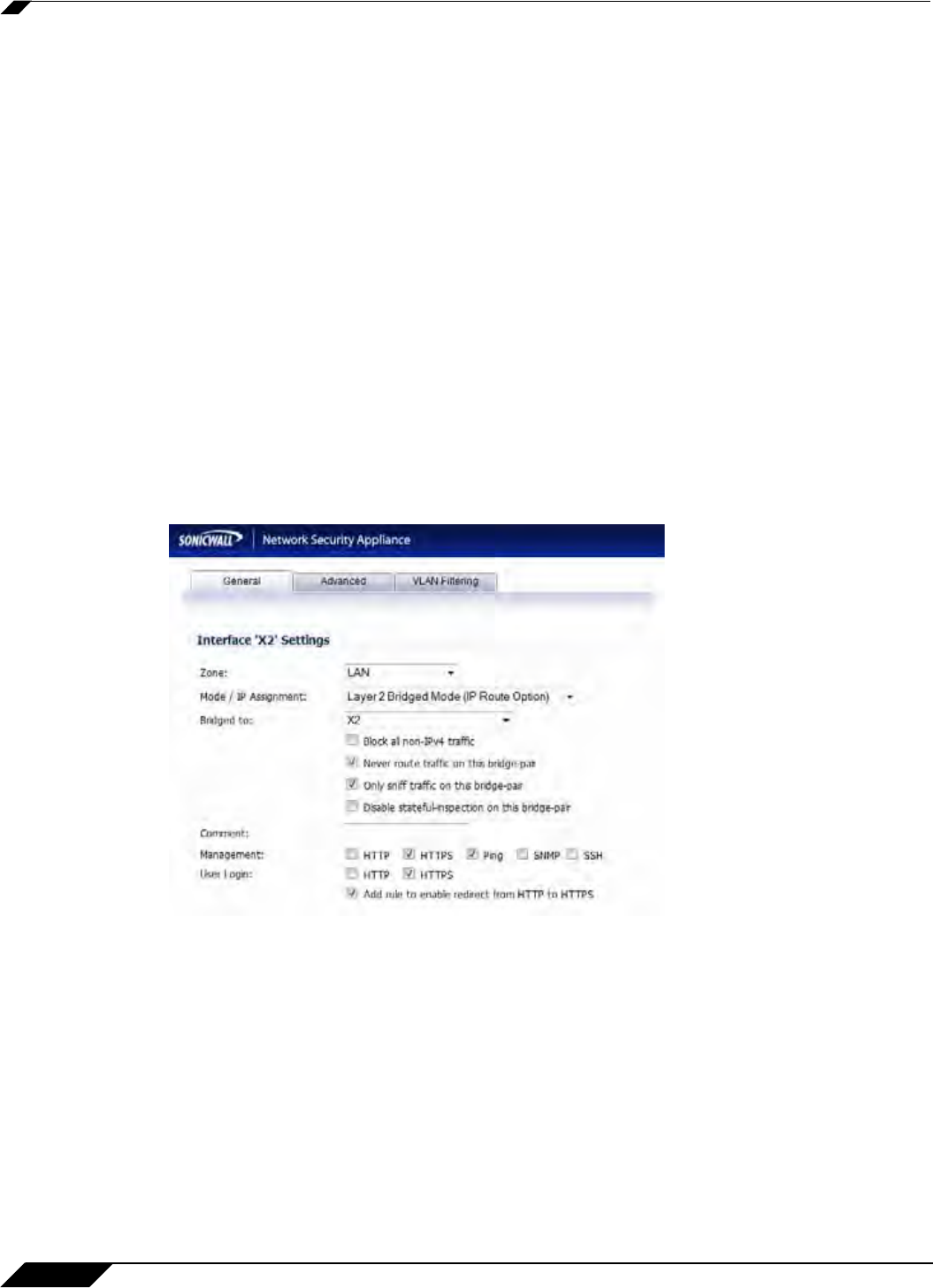
Step 3 In the Edit Interface dialog box on the General tab, select LAN from the Zone drop-down list.
Note that you do not need to configure settings on
the Advanced or VLAN Filtering tabs.
Step 4 In the IP Assignment drop-down list, select Layer 2 Bridged Mode.
Step 5 In the Bridged to drop-down list, select the X2 interface.
Step 6 Do not enable the Block all non-IPv4 traffic setting if you want to monitor non-IPv4 traffic.
Step 7 Select Never route traffic on this bridge-pair to ensure that the traffic from the mirrored
switch port is not sent back out onto the network. (The Never route traffic on this bridge-pair
setting is known as Captive-Bridge Mode.)
Step 8 Select Only sniff traffic on this bridge-pair to enable sniffing or monitoring of packets that
arrive on the L2 Bridge from the mirrored switch port.
Step 9 Select Disable stateful-inspection on this bridge-pair to allow TCP connections to pass
through the SonicWALL even if the device has not seen a valid and complete TCP handshake
sequence. This can be used for networks employing asymmetric packet paths for incoming and
outgoing traffic in which the SonicWALL does not see all traffic of the TCP flow. Use of this setting
is not recommended as it limits the SonicWALL’s ability to enforce TCP stateful and other
protections for the secured network.
Step 10 Configure management (HTTP, HTTPS, Ping, SNMP, SSH, User Logins, HTTP Redirects).
Step 11 Click OK.
Enabling and Configuring SNMP
When SNMP is enabled, SNMP traps are automatically triggered for many events that are
generated by SonicWALL Security Services such as Intrusion Prevention and Gateway Anti-
Virus.
More than 50 IPS and GAV events currently trigger SNMP traps. The SonicOS Log Event
Reference Guide contains a list of events that are logged by SonicOS, and includes the SNMP
trap number where applicable. The guide is available online at
http://www.sonicwall.com/us/Support.html by typing Log Event into the Search field at the top
of the page.


















