Fortinet 637 FortiWeb 5.0 Patch 6 Administration Guide
14.Convert the plain text file to a format recognizable by your network protocol analyzer
application.
You can convert the plain text file to a format (.pcap) recognizable by Wireshark (formerly
called Ethereal) using the fgt2eth.pl Perl script. To download fgt2eth.pl, see the Fortinet
Knowledge Base article Using the FortiOS built-in packet sniffer.
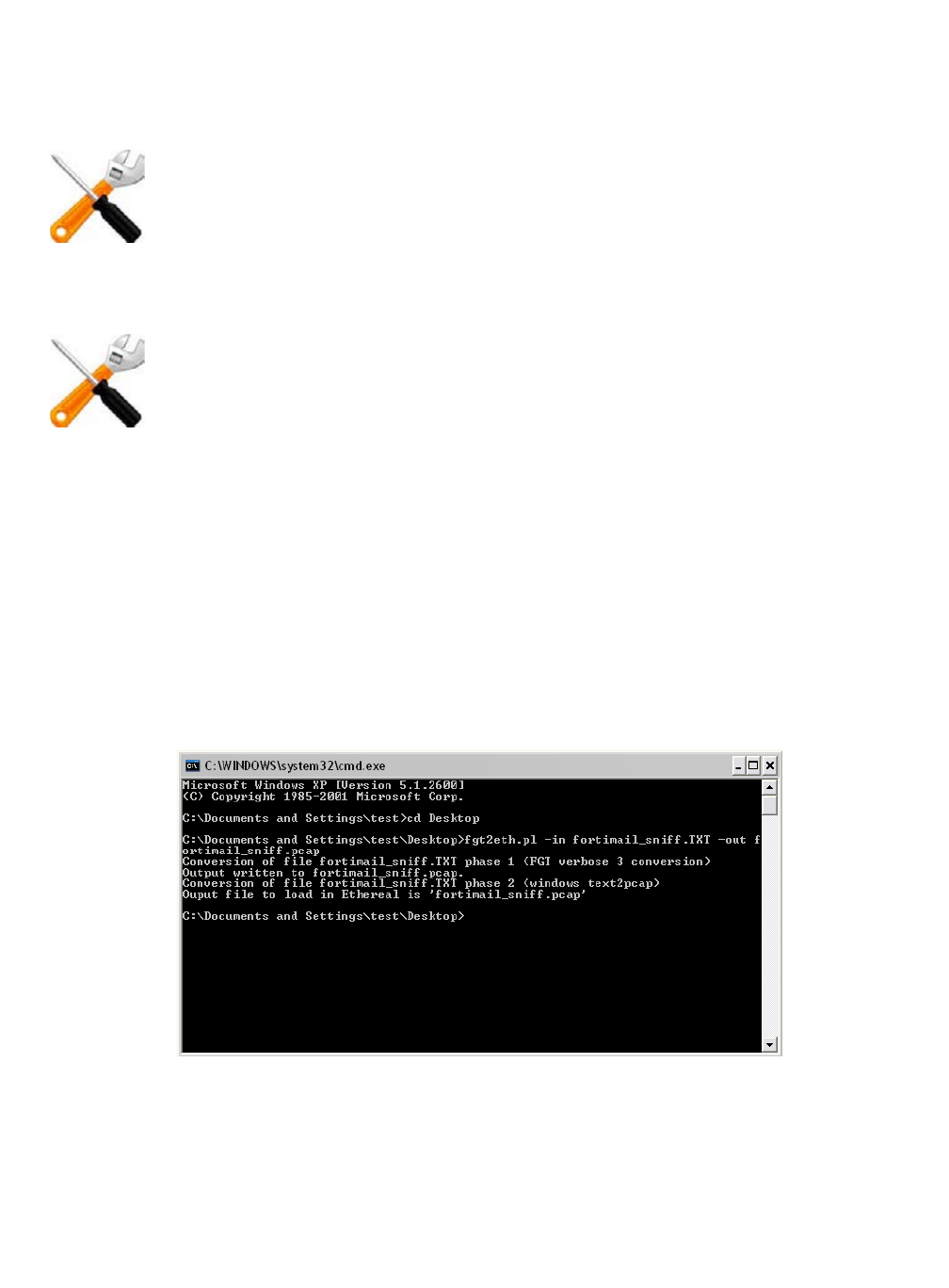
To use fgt2eth.pl, open a command prompt, then enter a command such as the following:
fgt2eth.pl -in packet_capture.txt -out packet_capture.pcap
where:
• fgt2eth.pl is the name of the conversion script; include the path relative to the current
directory, which is indicated by the command prompt
• packet_capture.txt is the name of the packet capture’s output file; include the
directory path relative to your current directory
• packet_capture.pcap is the name of the conversion script’s output file; include the
directory path relative to your current directory where you want the converted output to
be saved
Figure 87:Converting sniffer output to .pcap format
15.Open the converted file in your network protocol analyzer application. For further
instructions, see the documentation for that application.
The fgt2eth.pl script is provided as-is, without any implied warranty or technical support, and
requires that you first install a Perl module compatible with your operating system.
Methods to open a command prompt vary by operating system.
On Windows XP, go to Start > Run and enter cmd.
On Windows 7, click the Start (Windows logo) menu to open it, then enter cmd.