Fortinet 404 FortiWeb 5.0 Patch 6 Administration Guide
4. Click OK.
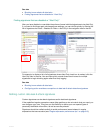
5. Click Add Target.
6. From Available Target, select which locations in the HTTP request (e.g. ARGS_NAMES for the
names of parameters or REQUEST_COOKIES for strings in the HTTP Cookie: header) will
be scanned for a signature match, then click the right arrow to move them into the Search In
area.
7. Click OK twice.
8. Repeat this procedure for each individual rule that you want to add.
• Redirect — Redirect the request to the URL that you specify in
the protection profile and generate an alert and/or log message.
Also configure Redirect URL and Redirect URL With Reason.
This option is available only if Direction is Signature Creation.
• Send 403 Forbidden — Reply with an HTTP 403 Access
Forbidden error message and generate an alert and/or log
message.This option is available only if Direction is Data
Leakage.
The default value is Alert.
Attack log messages contain Custom Data Leakage
Violation: <rule_name> or Custom Signature Creation
Violation: <rule_name> (depending on your configuration of
Direction) when this feature detects a possible attack.
Caution: This setting will be ignored if Monitor Mode is enabled.
Note: Logging and/or alert email will occur only if enabled and
configured. See “Logging” on page 542 and “Alert email” on
page 576.
Note: If you will use this rule set with auto-learning, you should
select Alert. If Action is Alert & Deny, or any other option that
causes the FortiWeb appliance to terminate or modify the request
or reply when it detects an attack attempt, the interruption will
cause incomplete session information for auto-learning.
Block Period Type the number of seconds that you want to block subsequent
requests from the client after the FortiWeb appliance detects that
the client has violated the rule.
This setting is available only if Action is set to
Period Block. T
he
valid range is from 1 to 3,600 (1 hour). The default value is 1. See
also “Monitoring currently blocked IPs” on page 606.
Severity When rule violations are recorded in the attack log, each log
message contains a Severity Level (severity_level) field.
Select which severity level the FortiWeb appliance will use when it
logs a violation of the rule:
•Low
•Medium
•High
The default value is High.
Trigger Action Select which trigger, if any, that the FortiWeb appliance will use
when it logs and/or sends an alert email about a violation of the
rule. See “Monitoring currently blocked IPs” on page 606.
Setting name Description