Fortinet 36 FortiWeb 5.0 Patch 6 Administration Guide
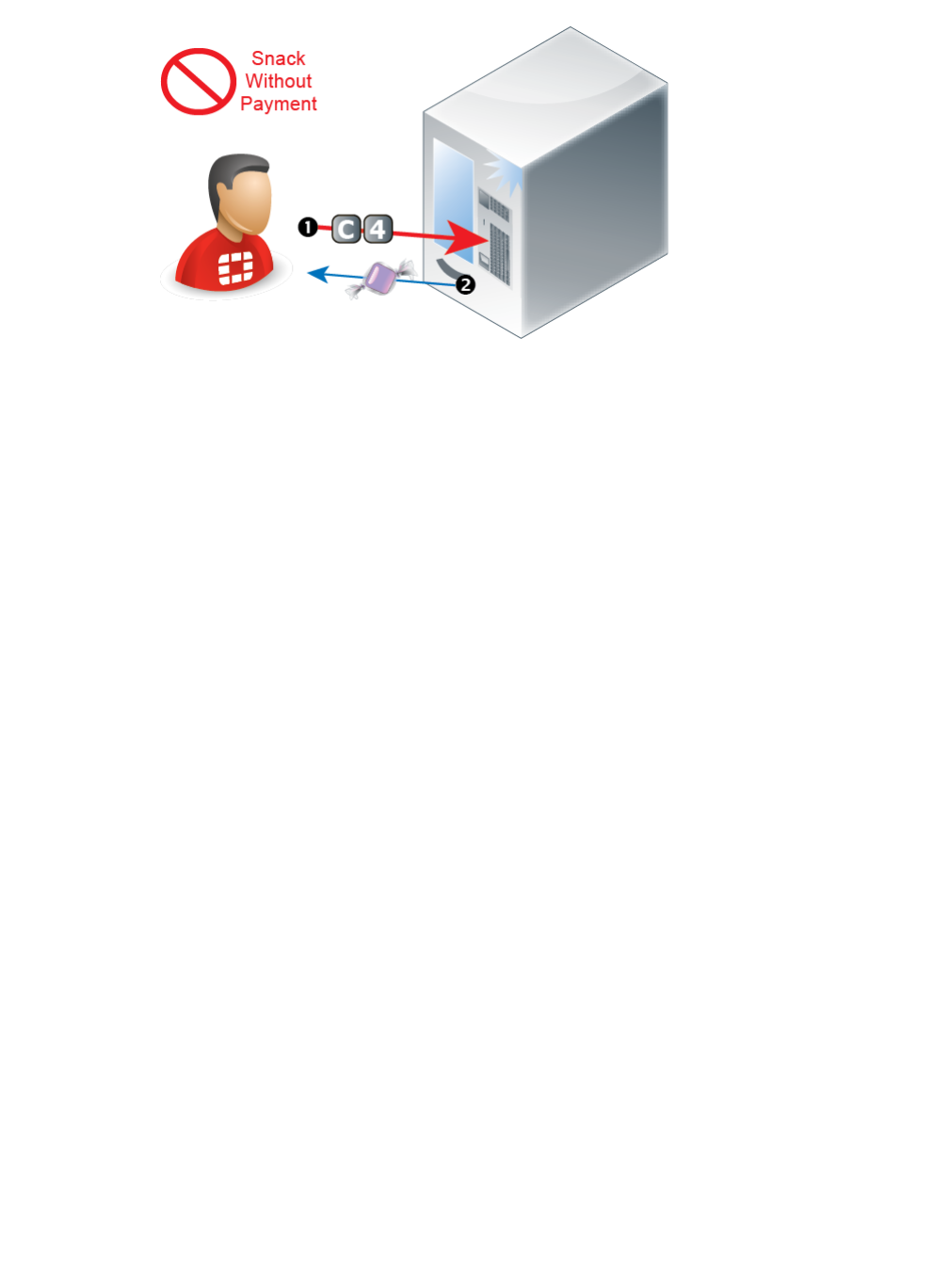
Figure 3: Invalid state transition in a vending machine
Similar to the working vending machine, in the TCP protocol, a connection cannot be
acknowledged (ACK) or data sent (PSH) before the connection has been initiated (SYN). There is
a definite order to valid operations, based upon the operation that preceded it. If a connection is
not already established — not in a state to receive data — then the receiver will disregard it.
Similar to the broken vendin
g machine, the naked HTTP protocol has no idea what the previous
HTTP request was, and therefore no way to predict what the next one might be. Nothing is
required to persist from one request to the next. While this was adequate at the time when
HTTP was initially designed, when it purely needed to retrieve static text or HTML documents,
as the World Wide Web evolved, this was no longer enough. Static pages evolved into dynamic
CGI-generated and JavaScripted pages. Dynamic pages use programs to change the page.
Scripted pages eventually evolved to fully-fledged multimedia web applications with their own
client-server architecture. As pages became software in their own right, a need for sessions
arose.
When a web application has its own native authentication, the session may correspond directly
wit
h it
s authentication logs — server-side sessions may start with a login and end with a
logout/session timeout. Within each session, there are contexts that the software can use to
determine which operations make sense. For example, for each live session, a web application
might remember:
• Who is the client? What is his/her user name?
• Where
is the client?
• What pages has the client already seen today?
• What forms has the client already completed?
However, sessions alone are not
en
ou
gh to ensure that a client’s requested operations make
sense. The client’s next page request in the session could break the web application’s logic
unless requests are restricted to valid ones.
For example, a web application session may remember that a client has authenticated. But
unless it also know
s what pages that client is authorized to use, there might be nothing to
prevent that person from ignoring the links on the current web page and entering a
non-authorized URL into their web browser to steal secret information.


















