Fortinet 634 FortiWeb 5.0 Patch 6 Administration Guide
• 2 — All of the output from 1, plus the packet payload in both hexadecimal and ASCII.
e.g.:
• 3 — All of the output from 2, plus the link layer (Ethernet) header. e.g.:
• <packets_int> is the number of packets the sniffer reads before stopping. Packet
capture output is printed to your CLI display until you stop it by pressing Ctrl+C, or until it
reaches the number of packets that you have specified to capture.
For example, you might capture all TCP port 443 (typically HTTPS) traffic occurring through
port1, regardless of its source or destination IP address. The capture uses a high level of
verbosity (indicated by 3).
A specific number of packets to capture is not specified. As a result, the packet capture
cont
inues until the administrator presses Ctrl+C. The sniffer then confirms that five packets
were seen by that network interface.
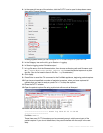
interfaces=[port2]
filters=[none]
0.915616 172.20.130.16.2264 -> 172.20.130.15.42574: udp 124
0x0000 4500 0098 d27d 4000 4011 0b8f ac14 8210 E....}@.@.......
0x0010 ac14 820f 08d8 a64e 0084 b75a 80e0 3dee .......N...Z..=.
0x0020 71b8 d617 38fa 3fd8 419b 5006 053c 99c1 q...8.?.A.P..<..
0x0030 e961 93bc 21c9 3197 a030 a709 76dc 0ed8 .a..!.1..0..v...
0x0040 98f8 ceef 6afb e7f2 7773 98e1 5ef7 bfbf ....j...ws..^...
0x0050 2f0d 726f 70cf 26cd d986 392f 4a0b f97b /.rop.&...9/J..{
0x0060 b84f 932d 3043 cbdd c2dc da77 0b73 70fc .O.-0C.....w.sp.
0x0070 158a 1868 eee0 793b c09e 7dc0 59f5 787c ...h..y;..}.Y.x|
0x0080 fc1a f25a dc18 735d f090 8e05 c3e8 c14f ...Z..s].......O
0x0090 3466 57c0 4688 58b8 4fW.F.X.
interfaces=[port2]
filters=[none]
0.317960 172.20.130.16.2264 -> 172.20.130.15.42574: udp 31
0x0000 50e5 49e8 dc3d 000f 7c08 2ff5 0800 4500 P.I..=..|./...E.
0x0010 003b 2cad 4000 4011 b1bc ac14 8210 ac14 .;,.@.@.........
0x0020 820f 08d8 a64e 0027 ea3c 80e0 981e 7474 .....N.'.<....tt
0x0030 6ddf 38fa 3fd8 419b 6e06 00f0 8dd5 e01d m.8.?.A.n.......
0x0040 810a e049 e5e9 380a f8 ...I..8..
Packet capture can be very resource intensive. To minimize the performance impact on your
FortiWeb appliance, use packet capture only during periods of minimal traffic, with a local
console CLI connection rather than a Telnet or SSH CLI connection, and be sure to stop the
command when you are finished.