Fortinet 453 FortiWeb 5.0 Patch 6 Administration Guide
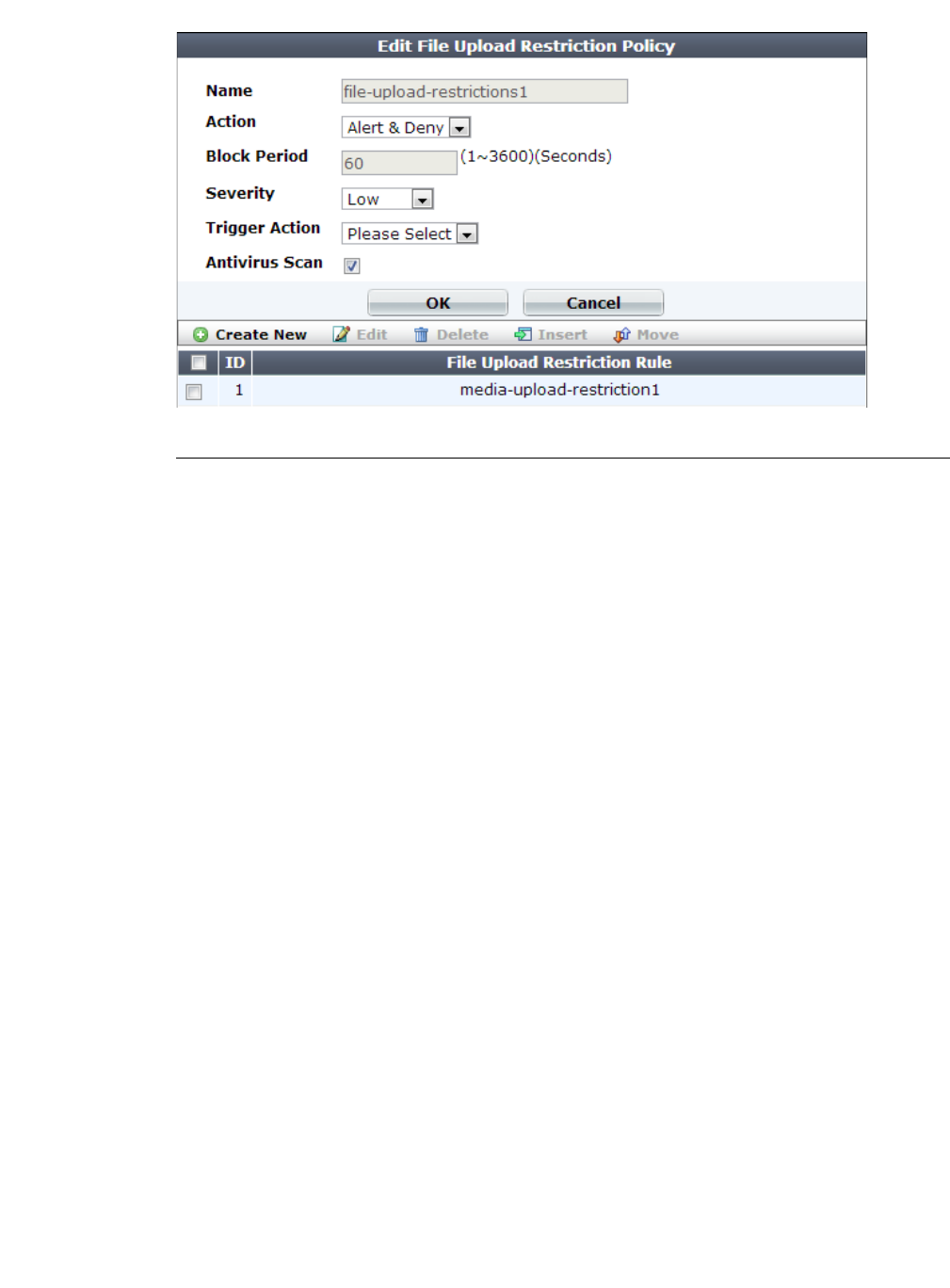
13.Configure these settings:
Setting name Description
Name Type a unique name that can be referenced in other parts of the
configuration. Do not use spaces or special characters. The
maximum length is 35 characters.
Action Select which action the FortiWeb appliance will take when it detects a
violation of the rule:
• Alert — Accept the connection and generate an alert email and/or
log message.
• Alert & Deny — Block the request (reset the connection) and
generate an alert and/or log message.
You can customize the web page that will be returned to the client
with the HTTP status code. See “Uploading a custom error page”
on page 467 or Error Message.
• Period Block — Block subsequent requests from the client for a
number of seconds. Also configure Block Period.
You can customize the web page that will be returned to the client
with the HTTP status code. See “Uploading a custom error page”
on page 467 or Error Message.
Note: If FortiWeb is deployed behind a NAT load balancer, when
using this option, you must also define an X-header that indicates
the original client’s IP (see “Defining your proxies, clients, &
X-headers” on page 266). Failure to do so may cause FortiWeb to
block all connections when it detects a violation of this type.
The default value is Alert.
Caution: This setting will be ignored if Monitor Mode is enabled.
Note: Logging and/or alert email will occur only if enabled and
configured. See “Logging” on page 542 and “Alert email” on
page 576.
Note: If you will use this rule set with auto-learning, you should select
Alert. If Action is Alert & Deny, or any other option that causes the
FortiWeb appliance to terminate or modify the request or reply when it
detects an attack attempt, the interruption will cause incomplete
session information for auto-learning.


















