Fortinet 277 FortiWeb 5.0 Patch 6 Administration Guide
Secure connections (SSL/TLS)
When a FortiWeb appliance initiates or receives an SSL or TLS connection, it will use
certificates. Certificates can be used in HTTPS connections for:
•encryption
• decry
ption and inspection
• authentication of clients
• authentication of servers
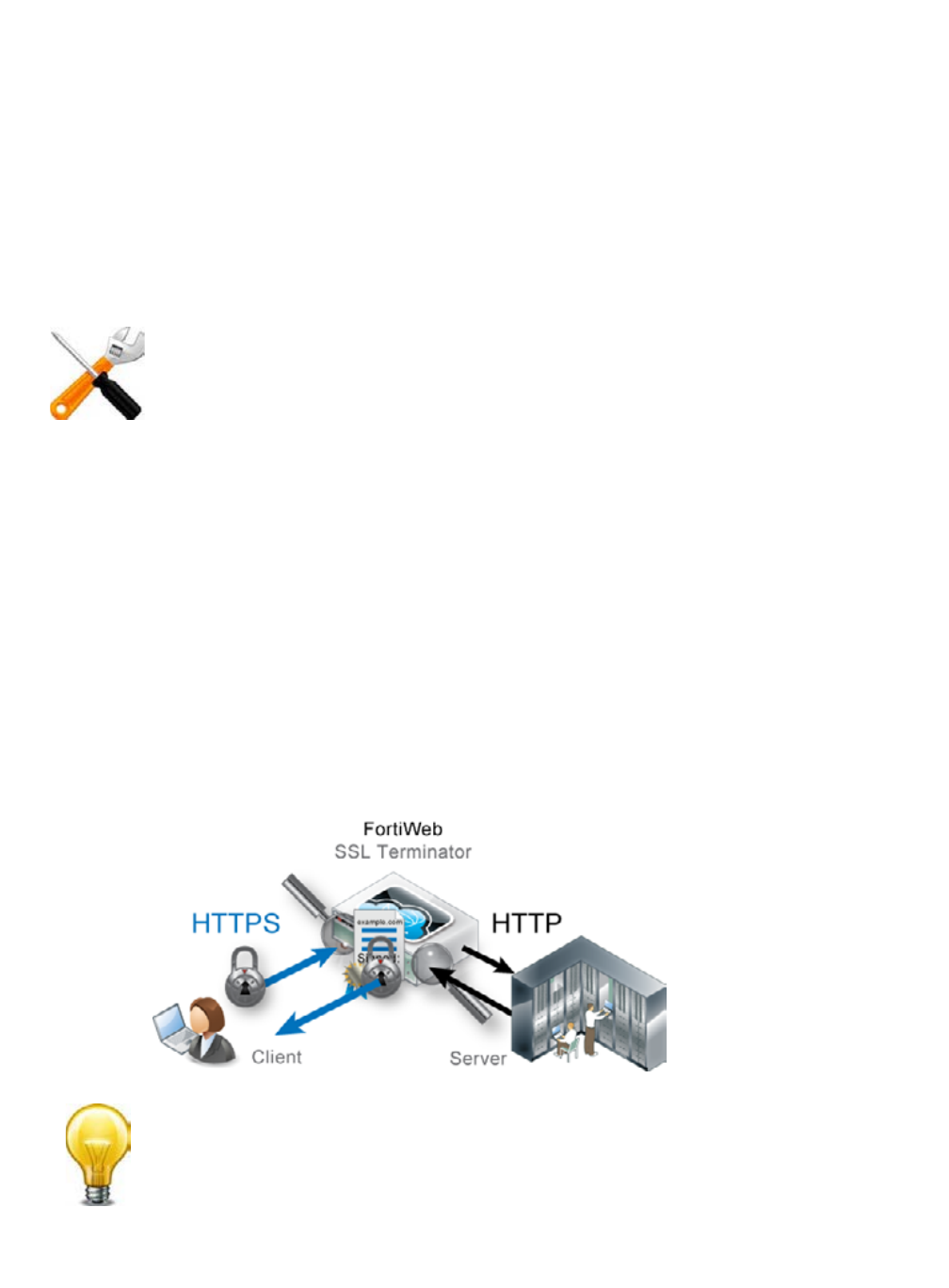
Offloading vs. inspection
Depending on the FortiWeb appliance’s operation mode, FortiWeb can act as the SSL/TLS
terminator: instead of clients having an encrypted tunnel along the entire path to a back-end
server, the client’s HTTPS request is encrypted/decrypted partway along its path to the server,
when it reaches the FortiWeb. FortiWeb then is typically configured to forward unencrypted
HTTP traffic to your servers. When the server replies, the server connects to the FortiWeb via
clear text HTTP. FortiWeb then encrypts the response and forwards it via HTTPS to the client.
In this way, FortiWeb bears the load for encryption processing instead of your back-end servers,
allo
wing
them to focus resources on the network application itself. This is called
SSL offloading.
FortiWeb may require you to provide certificates and CRLs even if your web sites’ clients do not
use HTTPS to connect to the web sites.
For example, when sending alert email via SMTPS or querying an authentication server via
LDAPS or STARTTLS, FortiWeb will validate the server’s certificate by comparing the server
certificate’s CA signature with the certificates of CAs that are known and trusted by the
FortiWeb appliance. See “Uploading trusted CAs’ certificates” on page 280 and “Revoking
certificates” on page 318.
SSL offloading can be associated with improved SSL/TLS performance. In hardware models
with specialized ASIC chip SSL accelerator(s), FortiWeb can encrypt and decrypt packets at
better speeds than a back-end server with a general-purpose CPU.


















