Fortinet 633 FortiWeb 5.0 Patch 6 Administration Guide
Packet capture
Packet capture, also known as sniffing or packet analysis, records some or all of the packets
seen by a network interface (that is, the network interface is used in promiscuous mode). By
recording packets, you can trace connection states to the exact point at which they fail, which
may help you to diagnose some types of problems that are otherwise difficult to detect.
FortiWeb appliances have a built-in sn
iffer. Packet capture on FortiWeb appliances is similar to
that of FortiGate appliances. To use the built-in sniffer, connect to the CLI and enter the
following command:
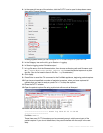
diagnose network sniffer packet [{any | <interface_name>}
[{none | '<filter_str>'} [{1 | 2 | 3} [<packets
_int>]]]]
where:
• <interface_name> is either the name of a network interface, such as port1, or enter any
for all interfaces.
• '<filter_str>' is the sniffer filter that specifies which protocols and port numbers that
you do or do not want to capture, such as 'tcp port 80', or enter none for no filters.
Filters use tcpdump syntax.
• {1 | 2 | 3} is an integer indicating whether to display the network interface names,
packet headers, and/or payloads for each packet that the network interface sends, receives,
or sees:
• 1 — Display the packet capture timestamp, plus basic fields of the IP header: the source
IP address, the destination IP address, protocol name, and destination port number.
Does not display all fields of the IP header; it omits:
• IP version number bits
• Internet header length (ihl)
• type of service/differentiated services code point (tos)
• explicit congestion notification
• total packet or fragment length
• packet ID
• IP header checksum
• time to live (TTL)
•IP flag
• fragment offset
•options bits
e.g.:
interfaces=[port2]
filters=[none]
0.655224 172.20.130.16.2264 -> 172.20.130.15.42574: udp 113