Fortinet 401 FortiWeb 5.0 Patch 6 Administration Guide
See also
• Blocking known attacks & data leaks
• Finding signatures that are disabled or “Alert Only”
Finding signatures that are disabled or “Alert Only”
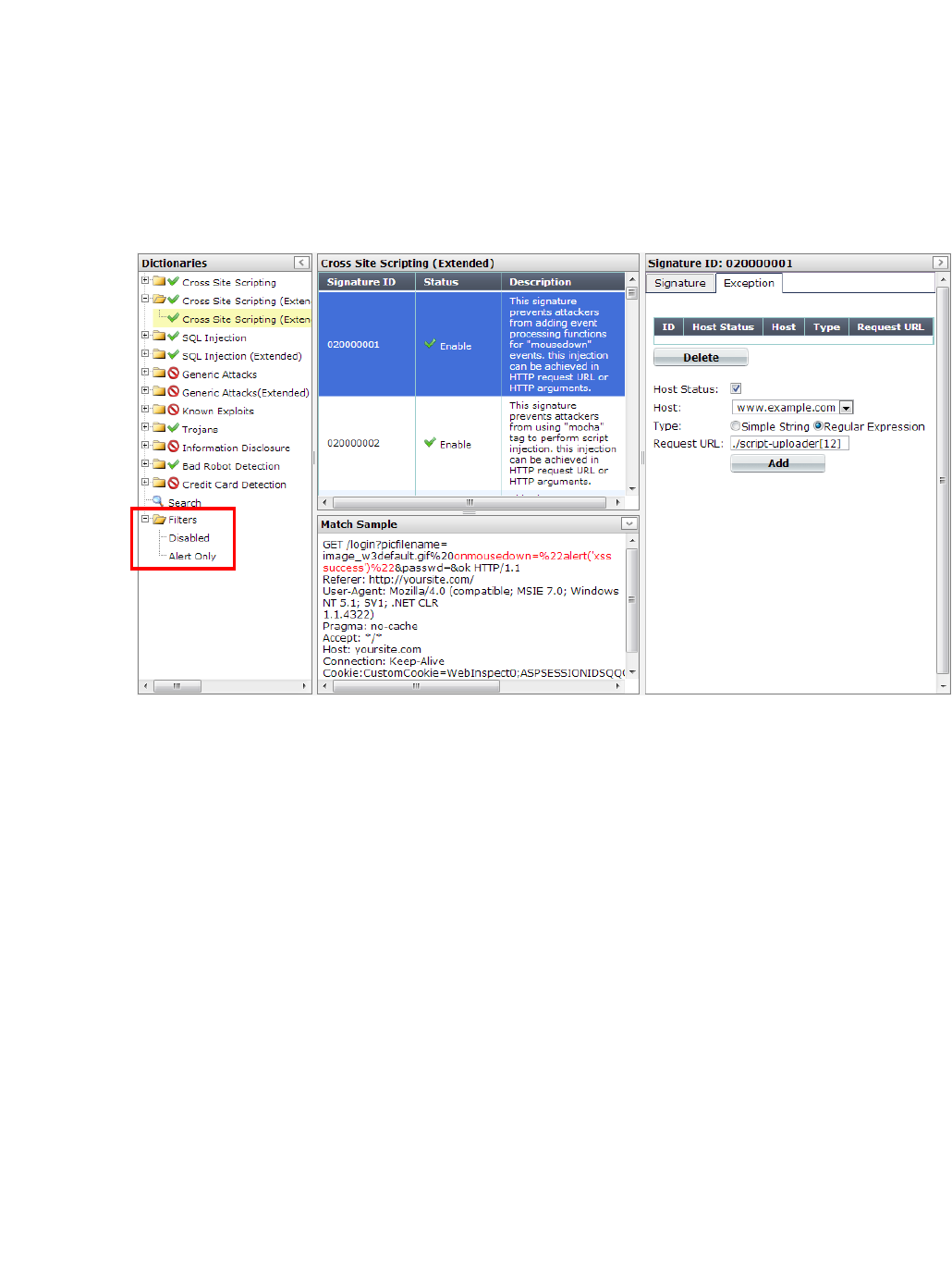
After you have disabled or overridden the actions of some individual signatures to be Alert Only,
if you need to find them again nd change those settings, you can do this quickly by filtering the
list of signatures via Filters > Disabled or Filters > Alert On
ly in the navigation tree on the left.
For example, to display a list of all signatures whose Alert Only check
box is marked, click the
Alert Only item in the tree. You can then quickly unmark these check boxes for multiple
signatures to begin blocking again rather than only logging.
See also
• Blocking
known attacks & data leaks
• Configuring action overrides or exceptions to data leak & attack detection signatures
Defining custom data leak & attack signatures
Custom signatures can be attack signatures and/or data leak signatures.
If the predefined regular expressions cause false positives or do not match what you need, you
can configure your own.
This gives you the flexibility to define your own special types of
personally identifiable information, as well as zero-day attacks.
Signatures should be crafted carefully to avoid performance issues inherent in regular
expres
sions that use recursion (see “Regular expression performance tips” on page 615).