Fortinet 611 FortiWeb 5.0 Patch 6 Administration Guide
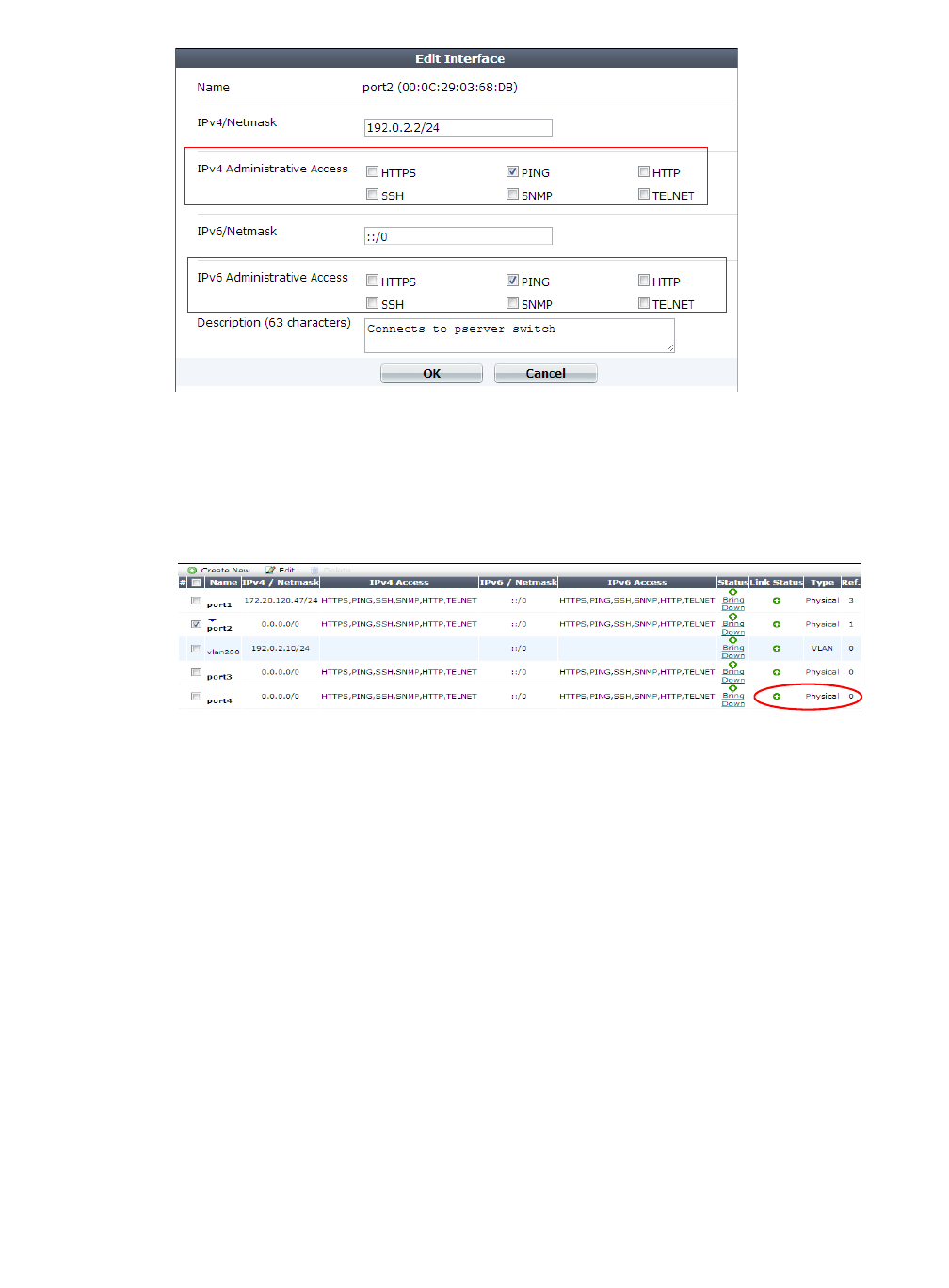
Figure 73:Restricting accepted administrative protocols in the Edit Interface dialog in
System > Network > Interface
Use only the most secure protocols. Disable PING, except during troubleshooting. Disable
HTTP, SNMP, and TELNET unless the network interface only connects to a trusted, private
administrative network. See “Configuring the network interfaces” on page 113.
• Disable all network interfaces that should not receive any traffic.
Figure 74:Disabling port4 in System > Network > Interface
For example, if administrative access is typically through port1, the Internet is connected to
port2, and web servers are connected to port3, you would disable (“bring down”) port4. This
would prevent an attacker with physical access from connecting a cable to port4 and
thereby gaining access if the configuration inadvertently allows it.
• Similar to applying trusted host filters to your FortiWeb administrative accounts, apply URL
access control rules to limit potentially malicious access to the administrative accounts of
each of your web applications from untrusted networks. See “Restricting access to specific
URLs” on page 321.
User access
• Authenticate users only over encrypted channels such as HTTPS, and require mutual
authentication — the web server or FortiWeb should show its certificate, but the client
should also authenticate by showing its certificate. Password-based authentication is less
secure than PKI authentication. For certificate-based client authentication, see “How to
apply PKI client authentication (personal certificates)” on page 293. For certificate-based
server/FortiWeb authentication, see “How to offload or inspect HTTPS” on page 283.
• Immediately revoke certificates that have been compromised. If possible, automate the
distribution of certificate revocation lists (see “Revoking certificates” on page 318).


















