Fortinet 224 FortiWeb 5.0 Patch 6 Administration Guide
input rule. Depending on your operation mode (see “Supported features in each operation
mode” on page 62), you might want to see:
• “Cookie Poisoning Detection” on page 473
• “Blockin
g known attacks & data leaks” on page 387
• “Validating parameters (“input rules”)” on page 421
• “Preventing tampering with hidden inputs” on page 430
• “Preventing brute force logins” on page 362
• “Specifying URLs allowed to initiate sessions” on page 415
Via a personal certificate
Alternatively or additionally to logging in by providing a password, clients can present an
X.509 v3 personal certificate. This can be a good choice for large organizations where:
• entering a password is onerous due to password length/complexity policies or the nature of
the devic
e (e.g. small touch screens on iPhone or Android smart phones, or highly secure
environments)
• you control the endpoint devices, so it is possible to install personal certificates
If your clients will connect to your web sites using HTTPS, you can configure FortiW
eb to
require clients to present a personal certificate during the handshake in order to confirm their
identities. This is sometimes called public key infrastructure (PKI) authentication (RFC 5280).
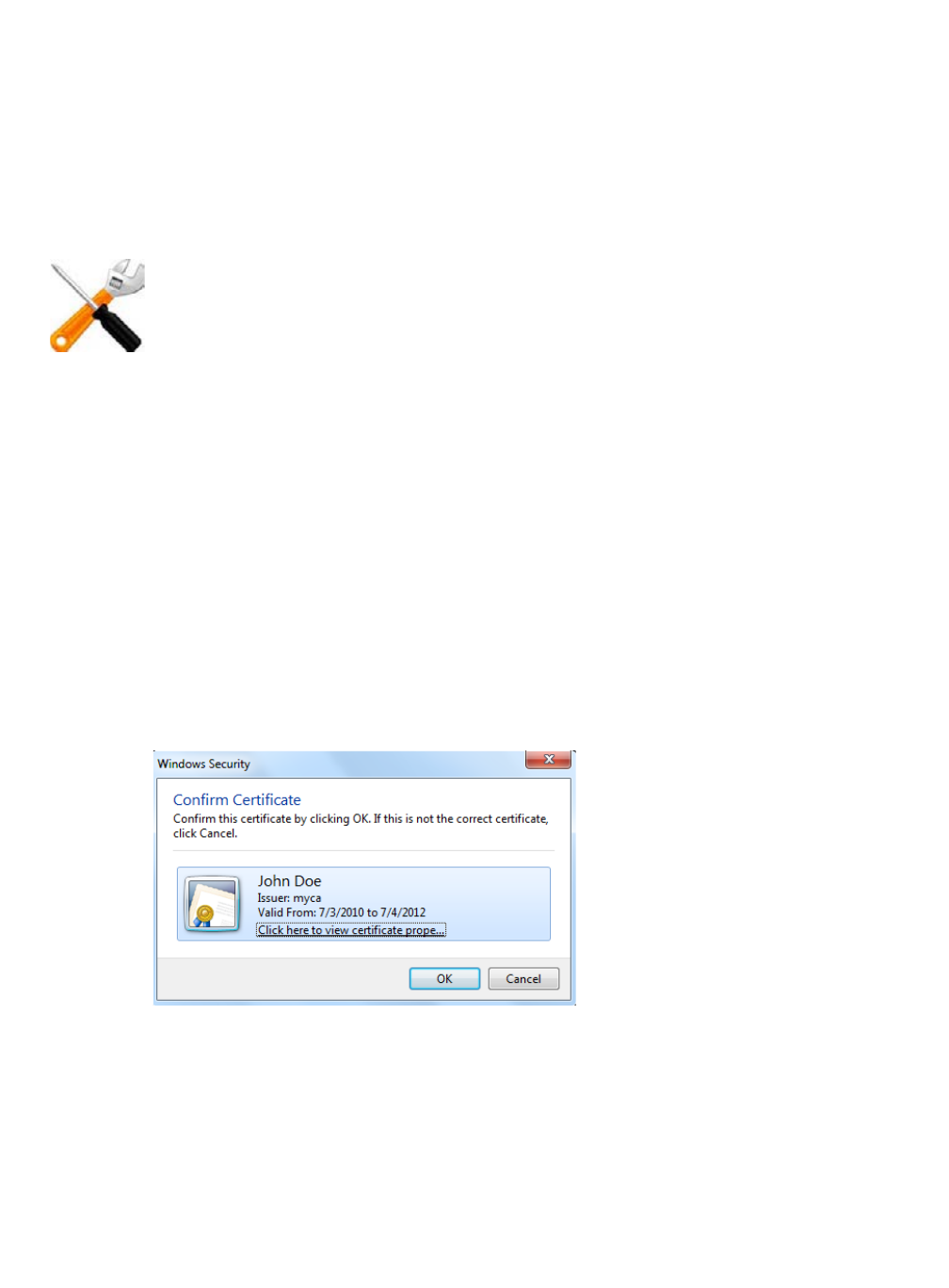
Figure 34:A personal certificate prompt in Microsoft Internet Explorer
For details, see “How to apply PKI client authentication (personal certificates)” on page 293.
If used within the content of HTTP, it is not as secure as HTTPS. For stronger protection, use
form-based authentication with HTTPS.


















