Fortinet 355 FortiWeb 5.0 Patch 6 Administration Guide
To configure TCP SYN flood protection
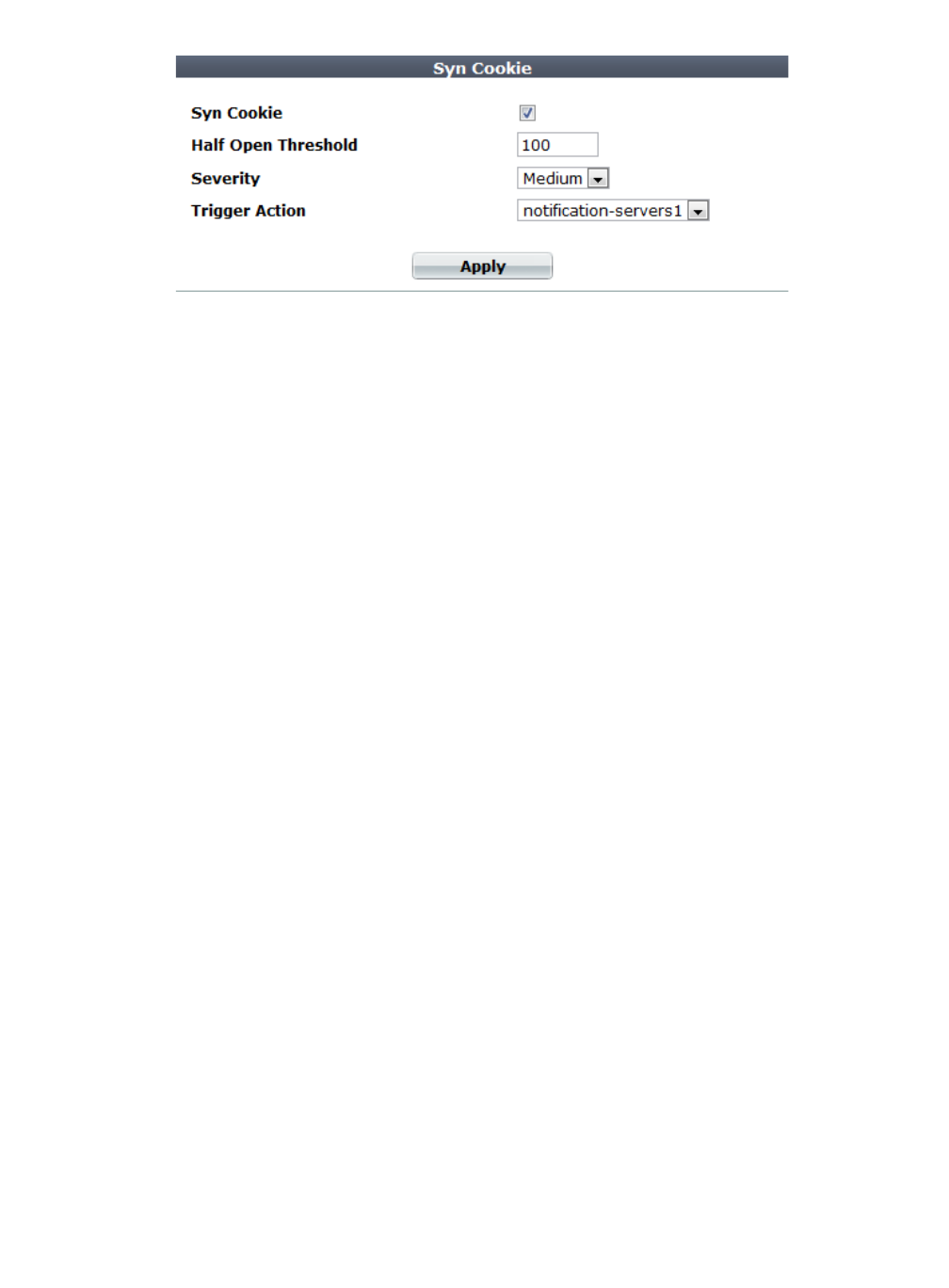
1. Go to DoS Protection > Network > Syn Cookie.
To access this part of the web UI, your administrator’s account access profile must have
Read and Write permission to items in the Web Protection Configuration category. For
details, see “Permissions” on page 47.
2. Enable Syn Cookie.
3. In Half Open Threshold, enter the maximum number of TCP SYN packets, including
retransmission, that may be sent per second to a destination address. If this threshold is
exceeded, the FortiWeb appliance assumes a DoS attack is occurring and ignores additional
traffic from that source IP address.
4. From the Severity drop-down list, select the severity level to include in logs and/or alert email
when this type of attack is detected.
5. From the Trigger Action drop-down list, select the trigger, if any, that defines which log
and/or alert email servers the FortiWeb appliance will use contact when the threshold is
exceeded (see “Configuring triggers” on page 557).
6. Click Apply.
Unlike other DoS protection features, you do not need to include this setting in a DoS
protection policy to make it effective. Once configured, the FortiWeb appliance applies SYN
flood protection immediately to all connections attempting to through it.
See also
• Limiting TCP connections per IP address
Grouping DoS protection rules
Before you can apply them in a server policy via a protection profile, you must first group DoS
prevention rules.
To configure a DoS protection policy
1. Before you can configure a DoS protection policy, you must first configure the rules that you
want to include:
• real browser enforcement rules (see “Preventing automated requests” on page 357)
• HTTP request flood prevention (see “Preventing an HTTP request flood” on page 347)
• HTTP request rate limit (see “Limiting the total HTTP request rate from an IP” on
page 339)
• TCP connections per session (see “Limiting TCP connections per IP address by session
cookie” on page 344)
• TCP connection flood prevention (see “Limiting TCP connections per IP address” on
page 351)


















