Fortinet 33 FortiWeb 5.0 Patch 6 Administration Guide
For more information on policy creation, see “DoS prevention” on page 338 and “Blacklisting
source IPs with poor reputation” on page 329.
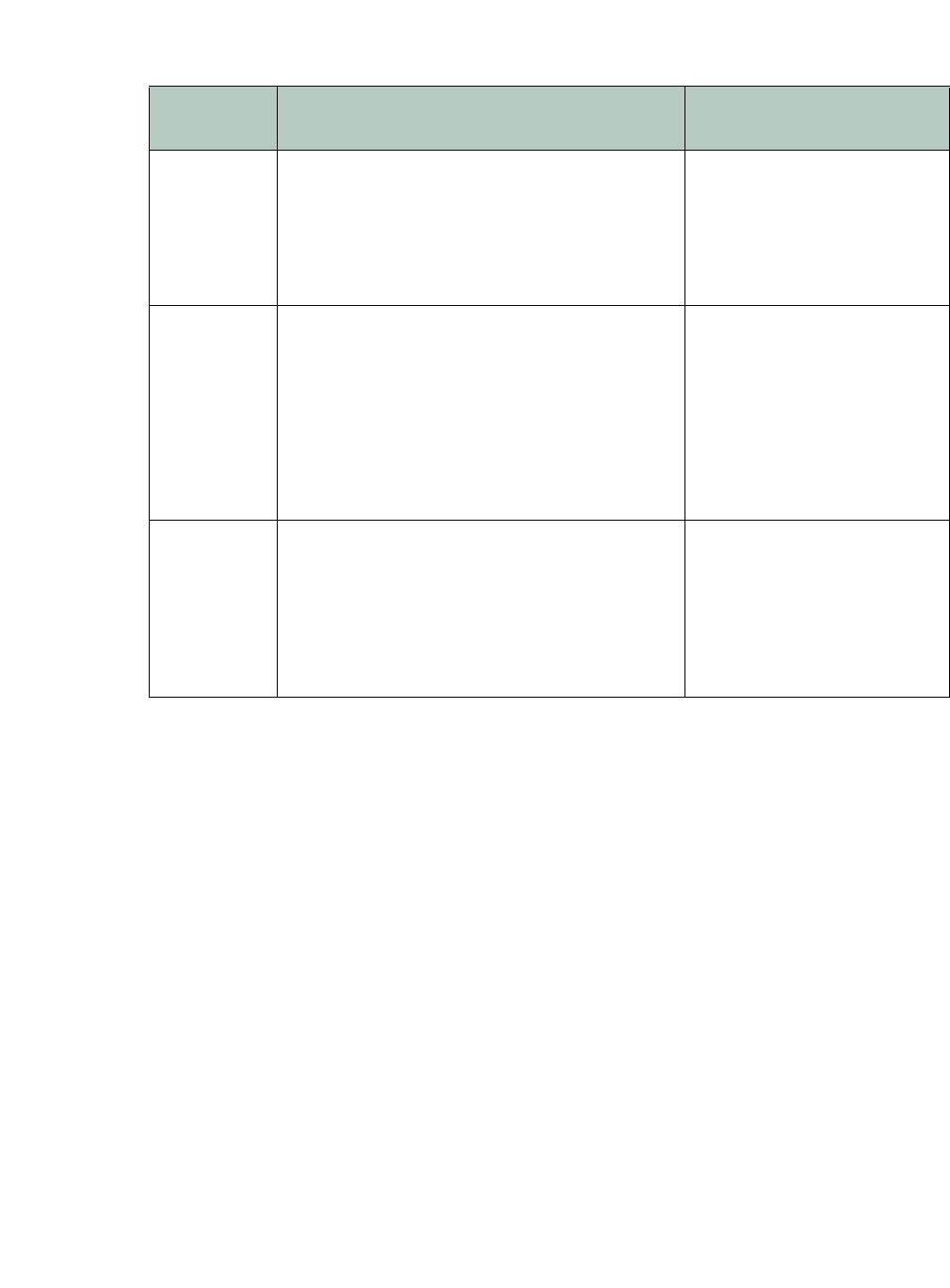
Table 3: DoS-related threats
Attack
Technique
Description FortiWeb Solution
Botnet Utilizes zombies previously exploited or
infected (or willingly participating),
distributed
usually globally, to simultaneously overwhelm
the target when directed by the command and
control server(s). Well-known examples include
LOIC, HOIC, and Zeus.
IP Reputation
Low-rate DoS Exploits TCP’s retransmission time-out (RTO)
by se
nding sho
rt-duration, high-volume bursts
repeated periodically at slower RTO
time-scales. This causes a TCP flow to
repeatedly enter a RTO state and significantly
reduces TCP throughput.
• TC
P Connection Number
Limit (TCP flood
prevention)
• HTTP Request Limit/sec
(HTTP flood prevention)
• TCP Connection Number
Limit (malicious IP
prevention)
Slow POST
attack
Sends multiple HTTP POST
requests with a
legitimate Content-Length: field. This tells
the web server how much data to expect. Each
POST message body is then transmitted at an
unusually slow speed to keep the connection
from timing out, and thereby consuming
sockets.
• URL Access
• Allow
Method


















