72 LogTag Analyzer
How secure is my data
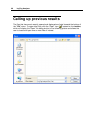
All LogTag files are encrypted and contain checks to detect if the file has been tampered
with since it was originally created. If the software detects that a file has been tampered
with, even by only one character or has become corrupted and therefore the data within
does not represent the data originally retrieved from the LogTag, the software will not
open the file and display the information within.
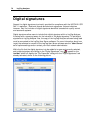
An additional validation and security feature of the LogTag is that it will automatically
insert error detection codes periodically during recordings, which are used to detect
corruption or manipulation of data. Whenever these detection codes for a block of
recordings fails its integrity validation test, the relevant readings become marked as non
validated readings. Non validated readings are displayed differently to validated readings
to indicate that they have failed their integrity test.
Non validated recordings typically occur in the scenarios following scenarios:
1 One or more readings within the non validated block of readings is not the genuine
recorded value.
2 The LogTag has been configured to perform continuous recordings and once the
memory within the LogTag has been fully used, will cause older recordings to be
overwritten, which will thereby invalidate the error detection code and integrity check
for the block of readings the older recordings been overwritten exist within. In this
scenario, it is not a problem that these recordings are non validated, rather it means
that the particular block of recordings has only the validation and integrity protection
offered by the communications between the LogTag and the computer system, which
is typically the same, if not better than the level of protection offered by every other
brand of logger available in the global market, that LogTag Recorders know of.
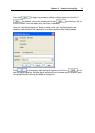
3 A communications or hardware failure has occurred during the transfer of the data
from the LogTag to the computer. In this scenario the problem is typically resolved by
trying to retrieve the recordings from the LogTag again, while ensuring the contacts
on the back of the LogTag are clean, that the contacts within the Interface Cradle are
clean and that the contacts within the Interface Cradle are returning evenly to their
normal position when the LogTag is removed.